14 Types Of Hackers Some Of Which Are Dangerous

14 Types Of Hackers Some Of Which Are Dangerous The hacker employee profile is as diverse as the ways people earn money or power, but they fall, roughly, into these 11 basic types. 1. the bank robber. once there were bank robbers and road. Here are ten hacking protection tips to help you stay safe online: keep personal information safe. make life harder for hackers by limiting the amount of personal information you share online, like your physical address, phone number, and other sensitive data. avoid public wi fi.
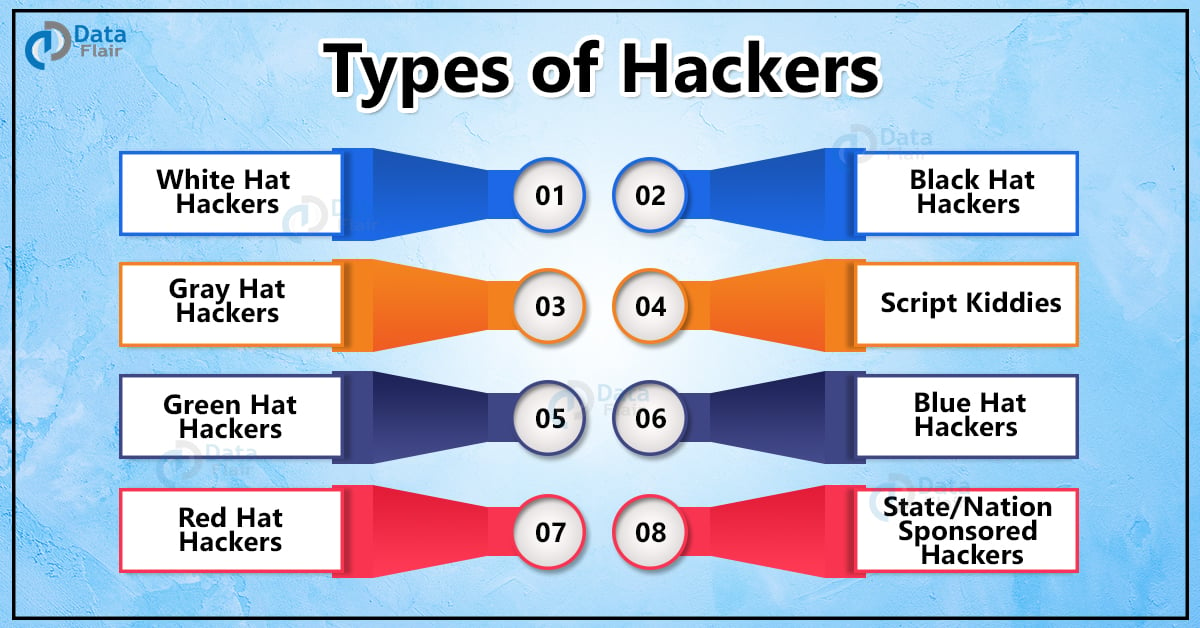
19 Types Of Hackers You Should Be Aware Of Dataflair Government agencies, information security teams, and companies like google, facebook, and uber hire white hats to use the force for good. they even reward them with “bug bounties” when they find critical bugs in the system. 3. gray hat hackers: mostly good, but technically still illegal. In fact, not all hackers are criminals — some are actually hired to stop criminals in their tracks. read on for a breakdown of 14 types of hackers to watch out for. 1. black hat: criminal hackers. a black hat hacker is a cybercriminal who breaks into computer systems with malicious or criminal intent. black hat hackers are probably what you. Black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of their targets before attacking, but they don’t intend to cause harm either. Final word. while this is a list of the most common hacker types, it’s not exhaustive. other notable types include blue hat hackers, green hat hackers, and red hat hackers, all of which can inflict untold damage if you’re not careful. this is why using security tools like vpns is highly recommended.

The Complete Guide To Ethical Hacking University Of Denver Boot Camps Black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of their targets before attacking, but they don’t intend to cause harm either. Final word. while this is a list of the most common hacker types, it’s not exhaustive. other notable types include blue hat hackers, green hat hackers, and red hat hackers, all of which can inflict untold damage if you’re not careful. this is why using security tools like vpns is highly recommended. Hacktivists: hacktivists are motivated by issues (political, economic, religious, and so on). some of these actors are solo actors, and some are in groups such as anonymous (known for a series of attacks on the church of scientology). these groups often use ddos (distributed denial of service) attacks and website defacements. According to the identity theft resource center's 2021 data breach report, the united states saw 1,862 data breaches in 2021, a record high. data breaches have long been on the rise. in perhaps the biggest ever, black hat hackers breached yahoo and stole 3 billion customer records from 2013 to 2014. and in october of 2016, hackers stole more.

Comments are closed.