Cism For Effective Third Party Risk Management Icert Global
Learn How To Implement Effective Third Party Risk Management Global The benefits of cism certification for third party risk management. obtaining a cism certification not only enhances an individual's credibility and expertise in information security risk management but also enables them to play a crucial role in managing third party cyber risks effectively. by leveraging the knowledge and skills gained through. Unlock the secrets to managing third party risks with our comprehensive guide on "cism for effective third party risk management." this video dives deep into.
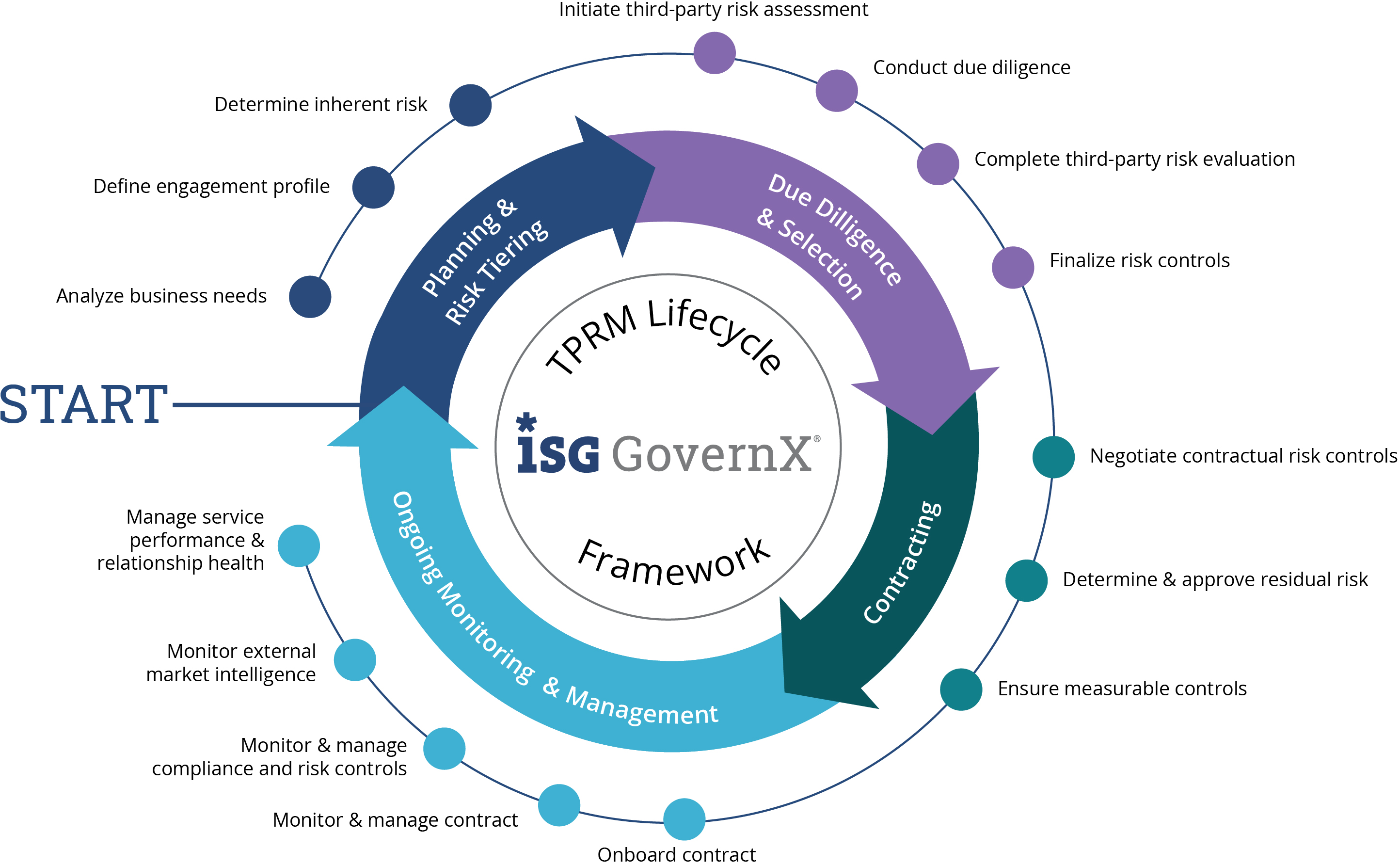
Effective Third Party Risk Management Isg Governx Cism for effective third party risk management discover how certified information security manager (cism) certification can elevate your approach to managing third party risks. While studying for the cism exam, focus on understanding key concepts rather than memorizing information. this will not only help you answer questions more effectively but also give you a deeper understanding of the material. pay close attention to topics such as risk management, information security governance, and incident management. Understanding cism. a key part of effective cybersecurity risk management is the cism certification. cism is a worldwide credential. it shows expertise in information security governance, risk management, and incident response. cism certified security professionals can build and apply strong cybersecurity strategies. 1. recognition and categorization of third party risk . effective third party risk management starts with understanding and categorizing the risks posed by different third party relationships. this involves creating a complete inventory of all vendors, suppliers, contractors, partners, and other third party entities that an organization engages.

Effective Third Party Risk Management Key Tactics And Success Factors Understanding cism. a key part of effective cybersecurity risk management is the cism certification. cism is a worldwide credential. it shows expertise in information security governance, risk management, and incident response. cism certified security professionals can build and apply strong cybersecurity strategies. 1. recognition and categorization of third party risk . effective third party risk management starts with understanding and categorizing the risks posed by different third party relationships. this involves creating a complete inventory of all vendors, suppliers, contractors, partners, and other third party entities that an organization engages. Managing supplier risk. organizations are increasingly reliant on third party suppliers to deliver business critical products and services to their clients and customers. they are also finding that failures by third parties can significantly impact their ability to operate effectively and tarnish their societal trust and reputation. Source: third party risk management outlook 2020, kpmg international 2020. tprm programs must have a well defined and thought through strategy, supported by a clearly articulated risk appetite. that way, programs have defined thresholds to manage against and report up to the board and senior management. — david hicks.

Comments are closed.