How To Conduct An Effective It Security Risk Assessment
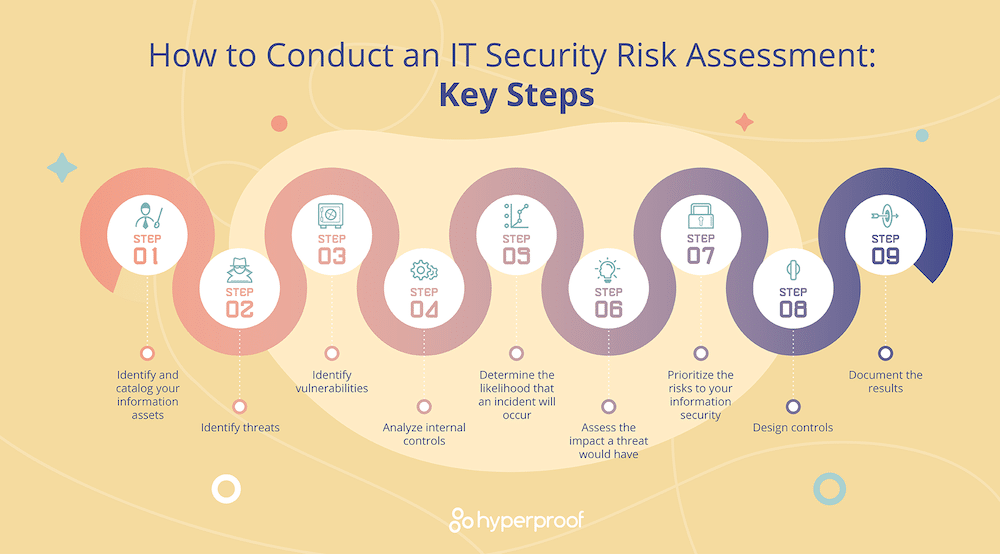
How To Perform A Successful It Risk Assessment Security Boulevard 7. document the results clearly and concisely in a report. the next step is to document the results clearly and concisely. so, here’s how it goes: a good risk assessment report presents the findings of threat and vulnerability assessments in a way that helps prioritize your remediation plan. Step 3: analyze risks and determine potential impact. now it is time to determine the likelihood of the risk scenarios documented in step 2 actually occurring, and the impact on the organization if it did happen. in a cybersecurity risk assessment, risk likelihood the probability that a given threat is capable of exploiting a given.
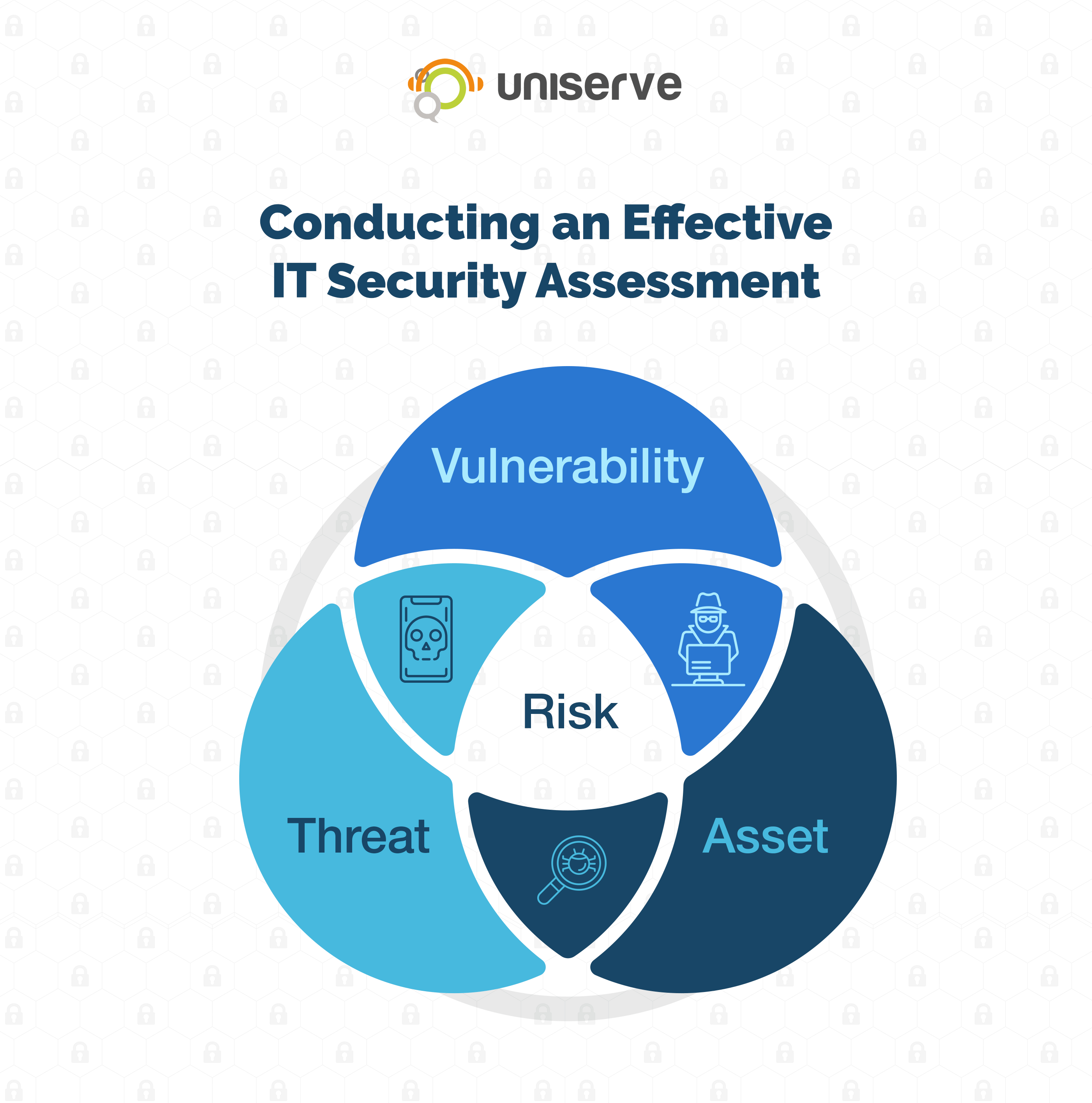
How To Conduct An Effective It Security Risk Assessment Here are seven key steps for conducting a comprehensive cyber risk assessment. 1. perform a data audit and prioritize based on value. establishing a comprehensive and current asset inventory is a foundational element of every company’s cybersecurity program. 1. identify and prioritize assets. the first step is to survey your it environment and catalog the information and systems within it. a good place to start is to run an asset discovery scan, using some form of network of vulnerability scanning tool. Identify and prioritize assets. the first step is to run a discovery scan to identify all the relevant assets in your it environment – using a vulnerability scanning tool. the goal here is to build a detailed picture of the technology you have, so you can prioritize areas at higher risk of a security incident. Finally, we presented a 5 step process for conducting risk assessments: determine scope —identify which parts of the organization and which systems need to be assessed. threat and vulnerability identification —scanning the relevant systems to identify vulnerabilities and security weaknesses.

Comments are closed.