How To Remediate Incidents With A Remote Workforce
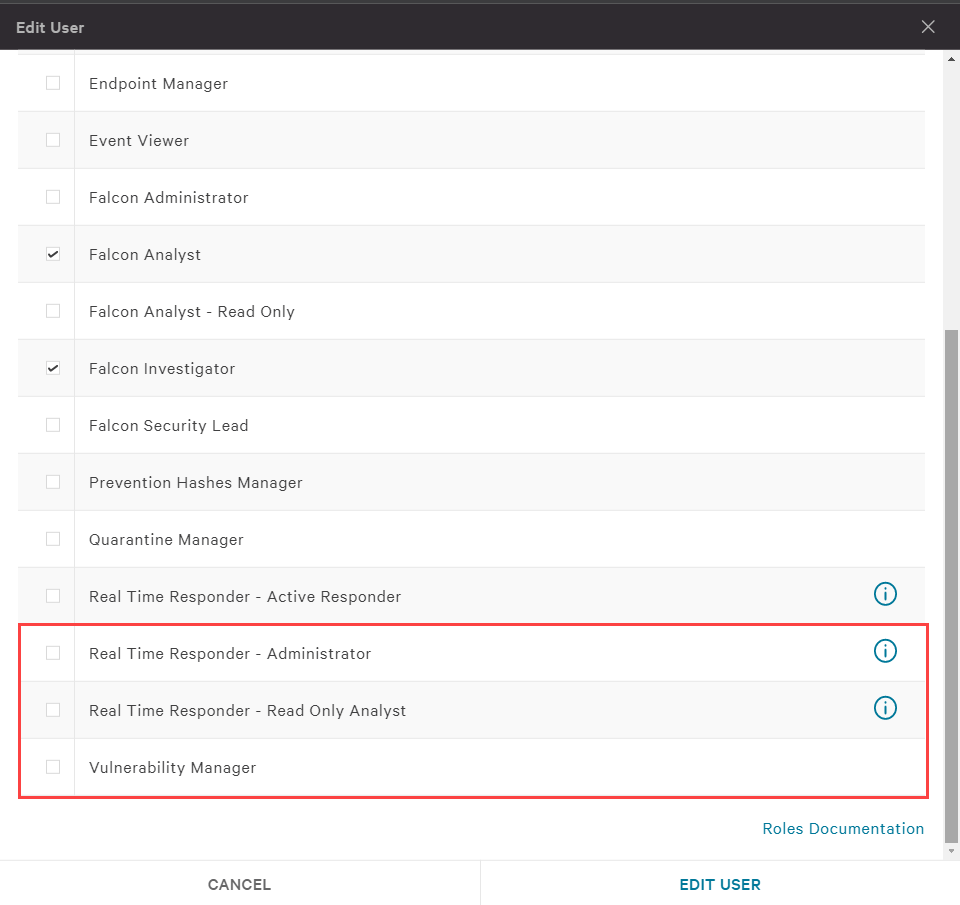
How To Remotely Remediate An Incident In this video we respond to an infected remote system that has been used as an attacker to move laterally via the corporate vpn. using crowdstrike's real tim. Remote workers drive the need for remote remediation the global pandemic and subsequent work from home trend has changed the way we respond to cybersecurity incidents. incident response , forensic analysis, and endpoint recovery needs to be delivered remotely, using real time response to actively contain threats and remediate endpoints with.

How To Remediate Incidents With A Remote Workforce Youtube In this session, you will learn: how the crowdstrike services team is able to respond to incidents from anywhere and at any time. how the team gains visibility into endpoints and is able to contain systems outside the corporate network. the advantages of using real time response to remotely remove malware without the need to rebuild systems. Working remote can be a forcing function to realize some best practices that all incident teams can benefit from, remote or not. at atlassian we’ve been practicing remote first incident management for years, as we have teams distributed around the globe. an alert about a power failure affecting a cloud server in oregon might have us waking up. Working remotely, or mixing that and in office work, can raise the risk of data breaches and different types of cyberattacks for various reasons, according to troha and other security experts. here are 10 of the most prominent cybersecurity risks associated with remote work and the work from anywhere movement. 1. expanded attack surfaces. A remote workforce security program is an essential component of a remote and hybrid work program. in this article, we explore the most significant security risks of remote work and offer some best practices that organizations and employees can implement to help manage and mitigate these risks. for example, requiring endpoint security solutions.
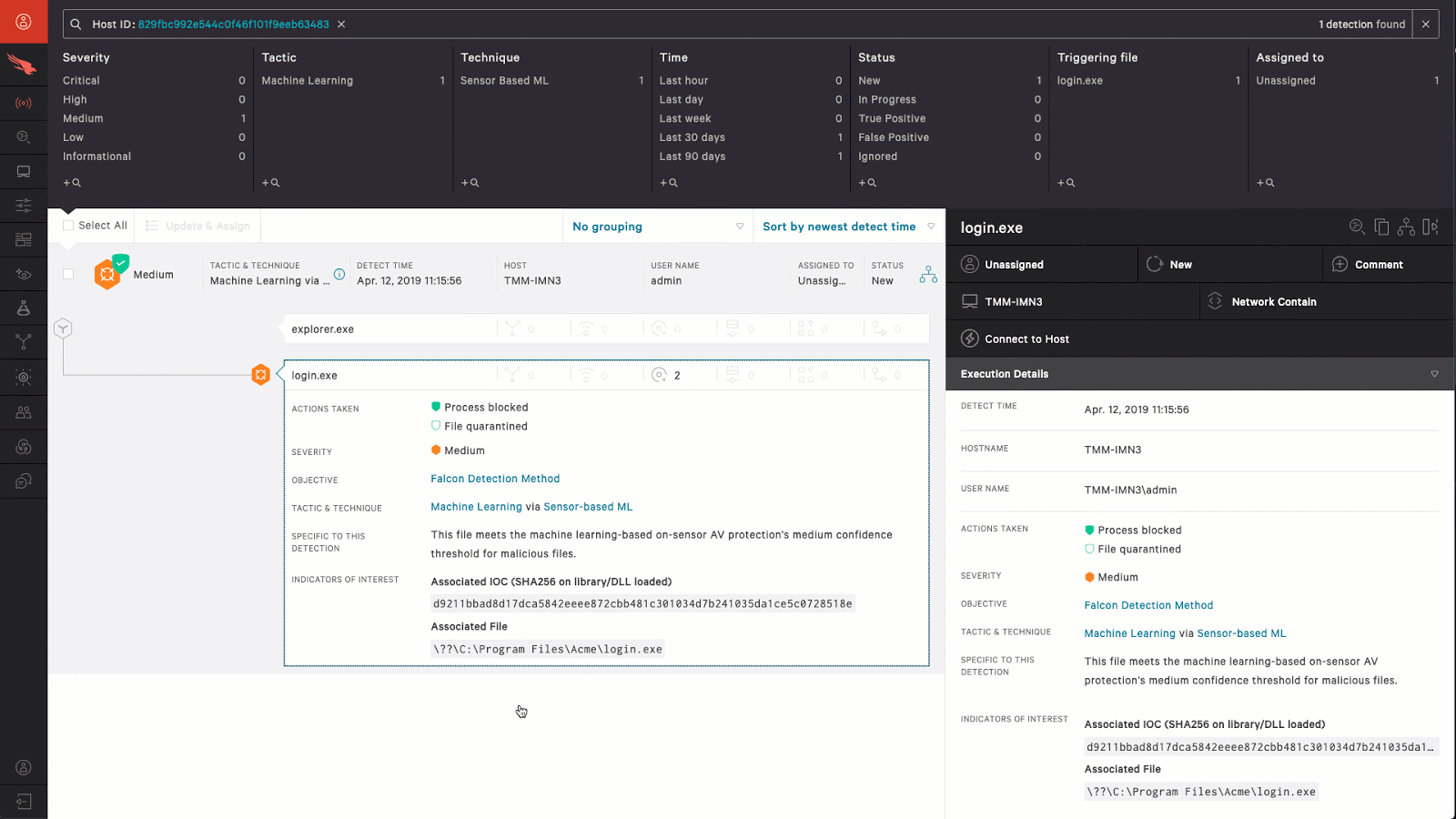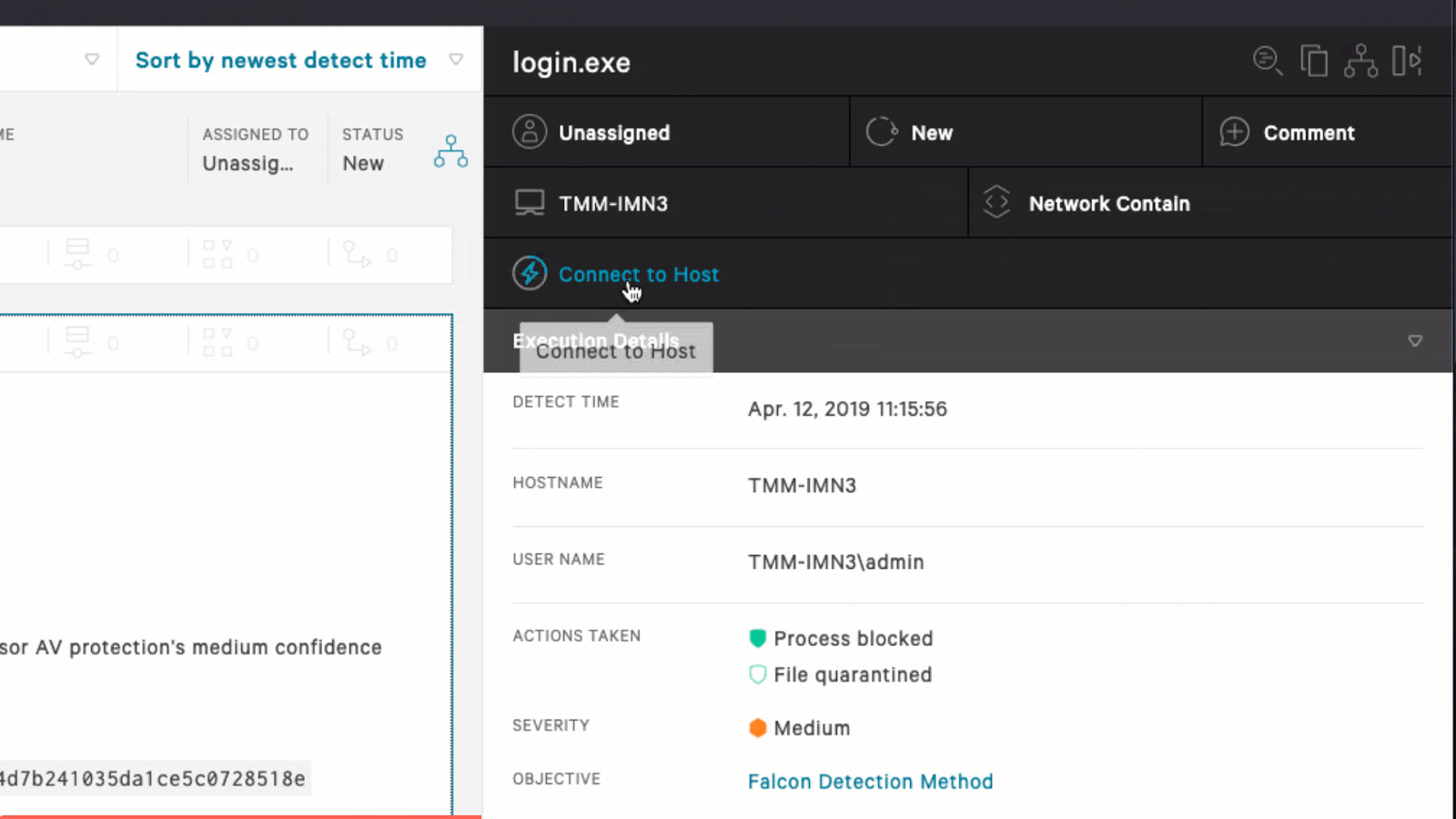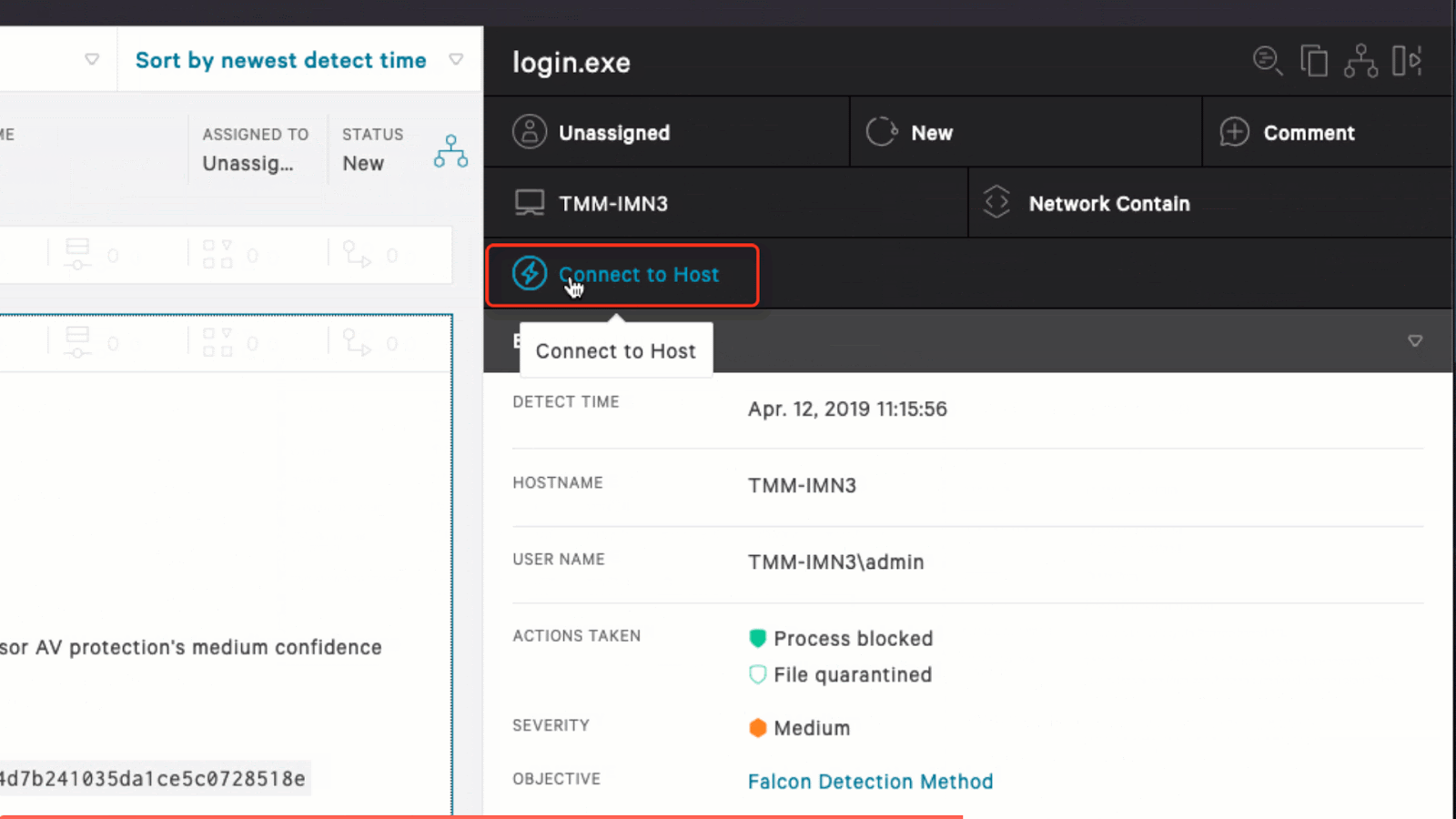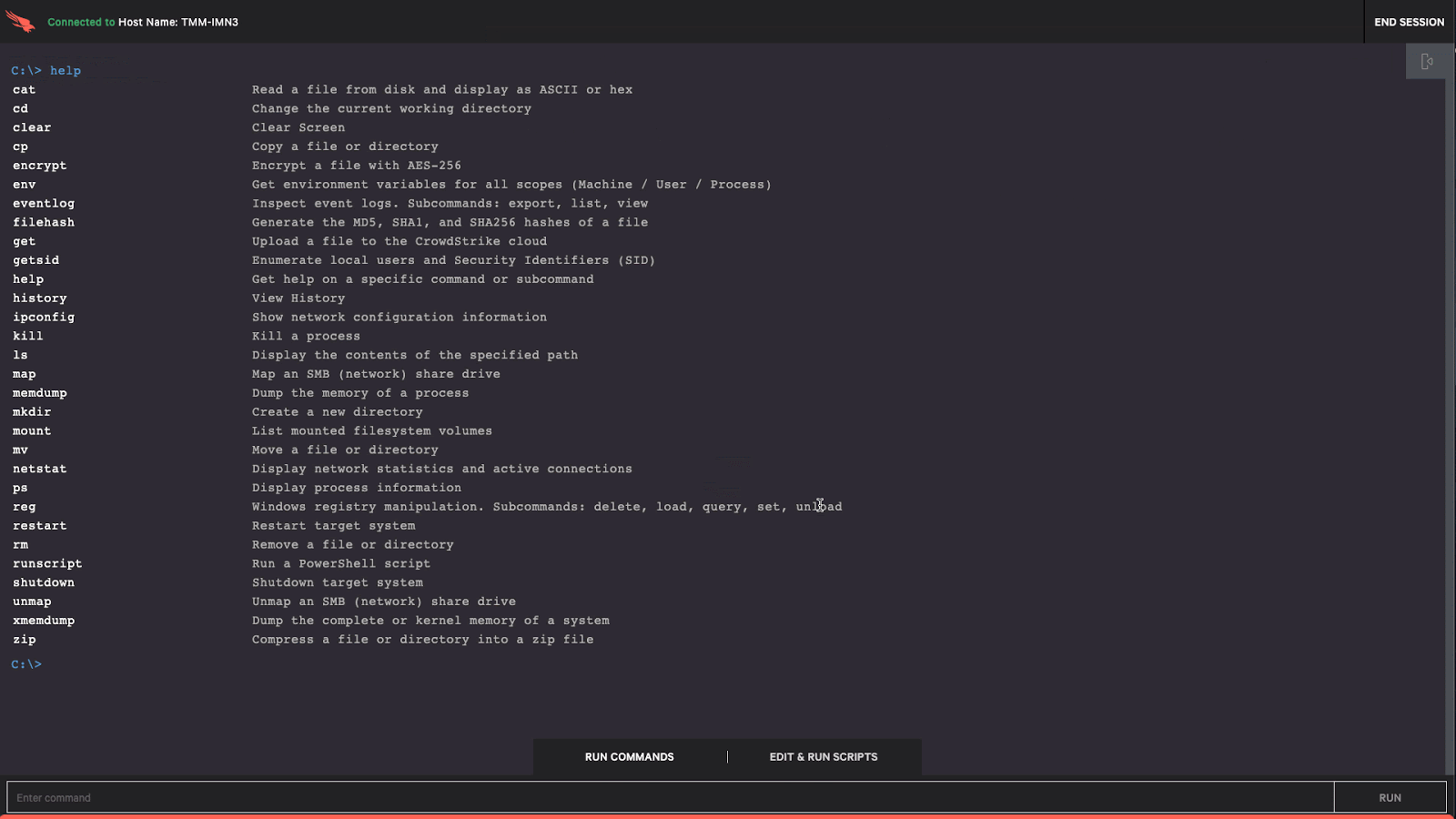
How To Remotely Remediate An Incident Working remotely, or mixing that and in office work, can raise the risk of data breaches and different types of cyberattacks for various reasons, according to troha and other security experts. here are 10 of the most prominent cybersecurity risks associated with remote work and the work from anywhere movement. 1. expanded attack surfaces. A remote workforce security program is an essential component of a remote and hybrid work program. in this article, we explore the most significant security risks of remote work and offer some best practices that organizations and employees can implement to help manage and mitigate these risks. for example, requiring endpoint security solutions. 5 tip 1: involve your stakeholders. one of the best tips to improve your incident reporting in a remote or hybrid work environment is to involve your stakeholders. your stakeholders are anyone who. Crowdstrike’s real time response enables you to execute precise, immediate remediation actions, and effectively stop breaches. contact us to learn how you can stop adversaries faster with crowdstrike real time response. in this resource, learn about how powerful and easy it can be to use real time response capabilities to mitigate malicious.

Make Remote Incident Response And Remediation A Reality Crowdstrike 5 tip 1: involve your stakeholders. one of the best tips to improve your incident reporting in a remote or hybrid work environment is to involve your stakeholders. your stakeholders are anyone who. Crowdstrike’s real time response enables you to execute precise, immediate remediation actions, and effectively stop breaches. contact us to learn how you can stop adversaries faster with crowdstrike real time response. in this resource, learn about how powerful and easy it can be to use real time response capabilities to mitigate malicious.

Comments are closed.