Malware Vs Ransomware What S The Difference And Risks
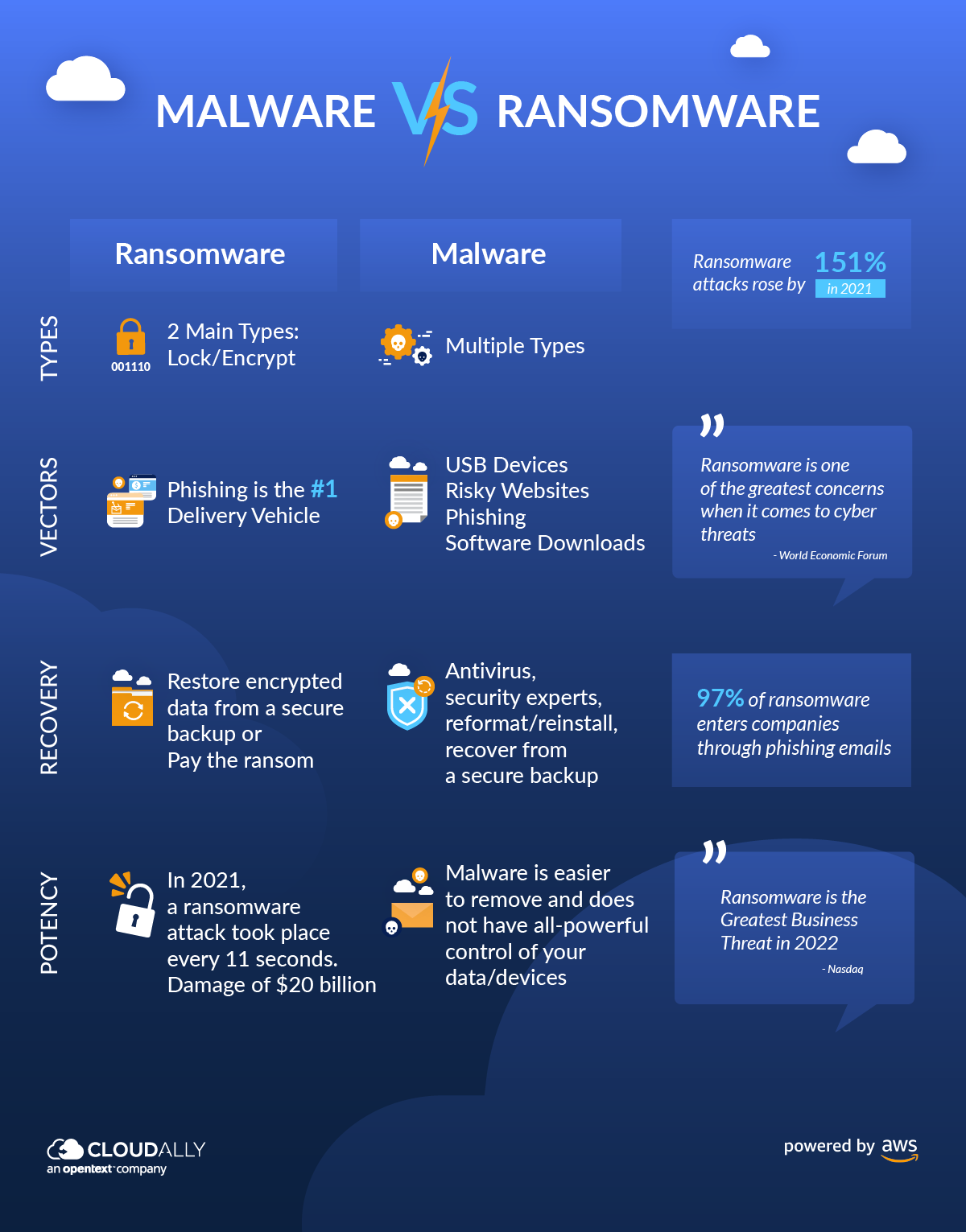
The Differences Between Malware Vs Ransomware Cloudally Malware vs ransomware: impacts and consequences. now that we’ve understood what malware and ransomware are, let’s discuss their impacts and potential consequences. effects of malware attacks. malware attacks can have a wide range of negative effects depending on the type of malware and the level of access it gains. Malicious adware aims to trick users into downloading other types of malware, such as spyware, to their devices. ransomware. this type of malware takes private digital resources hostage. attackers demand ransom payments in exchange for returning victims' access to their computer systems and data. rootkits.
Malware Vs Ransomware What S The Difference And Risks The difference between ransomware and malware primarily lies in their intent and impact. when comparing malware vs ransomware, it’s important to note that while all ransomware is malware, not all is ransomware. malware, an umbrella term, encompasses all malicious software, including ransomware, designed to harm a computer system or network. Ransomware is a type of malware identified by specified data or systems being held captive by attackers until a form of payment or ransom is provided. phishing is online scam enticing users to share private information using deceitful or misleading tactics. cisa offers a variety of tools and resources that individuals and organizations can use. While malware encompasses a wide range of malicious software, including ransomware, its purposes can vary from data theft to unauthorized access. ransomware, on the other hand, focuses on extortion and financial gain through the hostage taking of digital assets. from a cybersecurity perspective, defending against malware and ransomware requires. Once ransomware gains access to a computer, it works its way through the filesystem checking the types of files that it finds. if a file matches a built in list of file extensions, the malware encrypts the data that it contains, replaces the original with the encrypted version, and wipes any record of the original from the system.

Comments are closed.