Sim Swapping What Is It And How To Protect Yourself From It
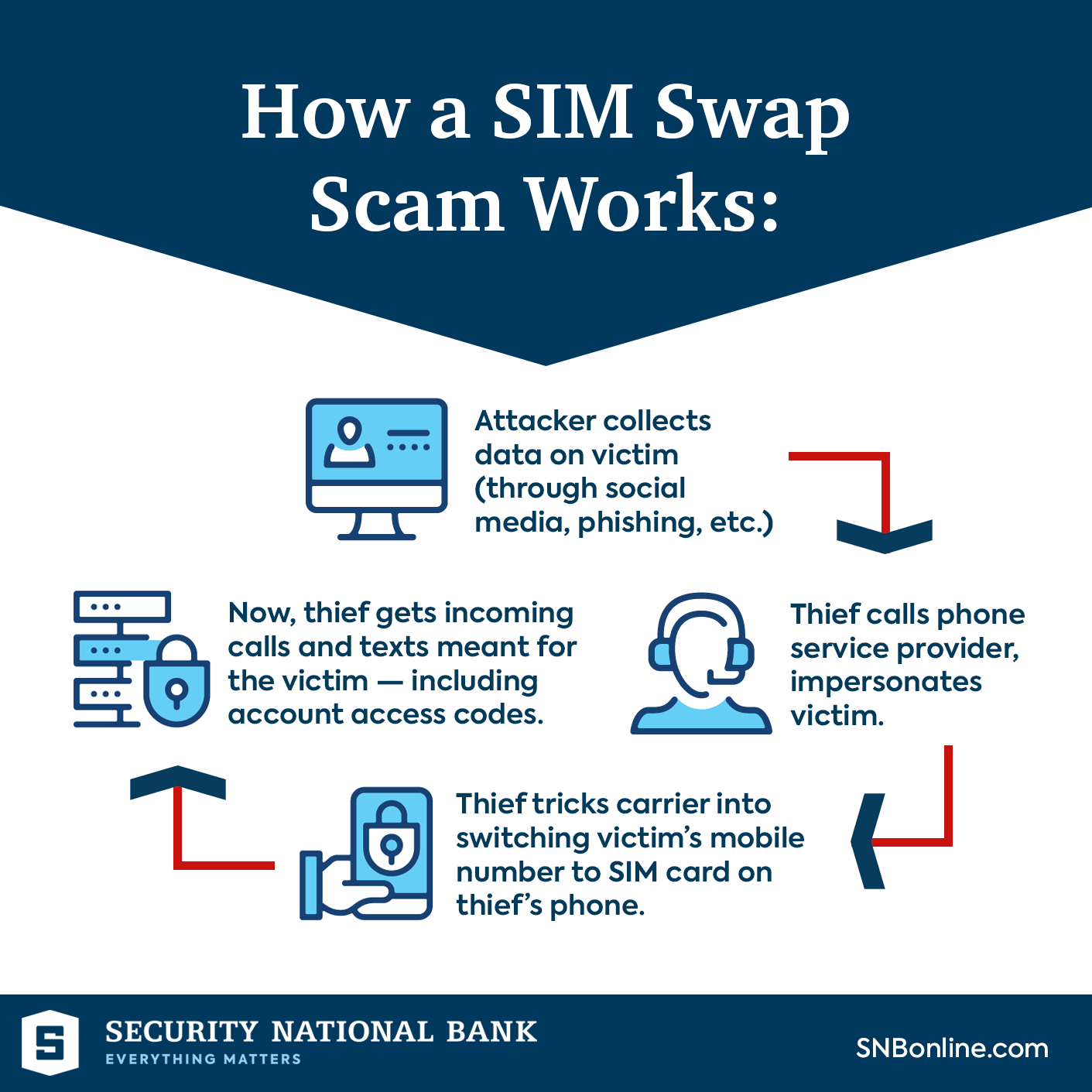
Sim Swap Fraud How To Protect Yourself SIM-swapping is a growing form of identity theft that goes beyond hacking into an email or social media account In this case, the thieves take over your phone number Any calls or texts go to them, That is why cybercriminals have created a new way to scam these people: SIM swapping This method takes advantage of two-factor authentication by tricking you into signing up for a new eSIM
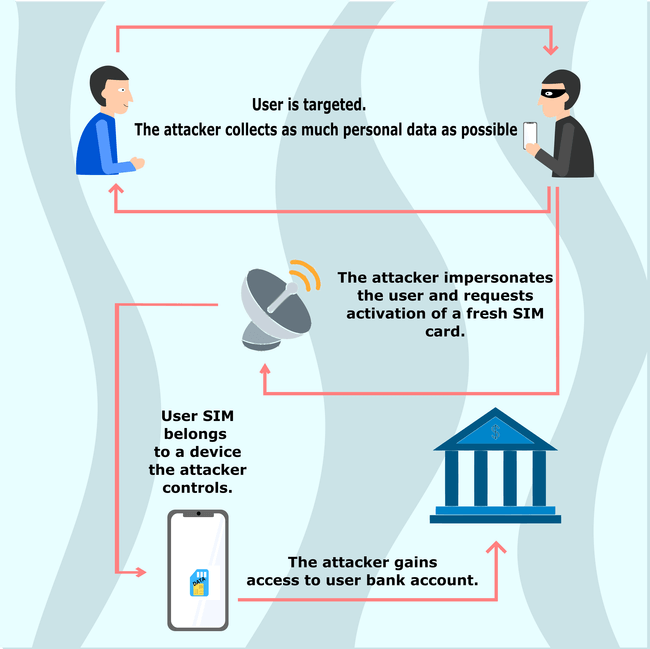
Sim Swapping What Is It And How To Protect Yourself From It SIM swapping (or SIM jacking is a good start in terms of keeping yourself safe and minimizing the risk of your own number getting stolen As always, to protect your data, be wary of following Virtual kidnapping is a type of extortion scheme where scammers use threats and manipulation to trick victims into paying a ransom to save a loved one they believe is in danger While individual phone users are ultimately responsible for how they engage with text messages, it takes a team effort to protect us all from threats like smishing attacks SMS providers help the Explore how ATO attacks work, how to identify them and learn good online practices you can adopt to protect your data, identity, and finances

How To Protect Yourself From Sim Swapping Experian While individual phone users are ultimately responsible for how they engage with text messages, it takes a team effort to protect us all from threats like smishing attacks SMS providers help the Explore how ATO attacks work, how to identify them and learn good online practices you can adopt to protect your data, identity, and finances The reason for activating a SIM card lock is due to SIM phishing Scammers use SIM phishing, also known as SIM swapping contact your carrier and verify yourself to get the PUK from them But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Despite this, data breaches aren't hard to protect yourself from — it just takes some care and skepticism Here's everything you need to know about data breaches, including how they work Ransomware is a common and serious threat Fortunately, there are several simple and effective ways to protect yourself Here are four steps you can take to shield yourself from any potential attacks
What Is A Sim Swap Attack How Can You Protect Yourself From It The reason for activating a SIM card lock is due to SIM phishing Scammers use SIM phishing, also known as SIM swapping contact your carrier and verify yourself to get the PUK from them But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Despite this, data breaches aren't hard to protect yourself from — it just takes some care and skepticism Here's everything you need to know about data breaches, including how they work Ransomware is a common and serious threat Fortunately, there are several simple and effective ways to protect yourself Here are four steps you can take to shield yourself from any potential attacks Extreme heat waves can cause cases of dehydration, exhaustion, heat stroke and even death But the air temperature isn't the only factor in how dangerous a hot day is; there's also another measure

Sim Swap Scam What It Is And How To Protect Yourself Despite this, data breaches aren't hard to protect yourself from — it just takes some care and skepticism Here's everything you need to know about data breaches, including how they work Ransomware is a common and serious threat Fortunately, there are several simple and effective ways to protect yourself Here are four steps you can take to shield yourself from any potential attacks Extreme heat waves can cause cases of dehydration, exhaustion, heat stroke and even death But the air temperature isn't the only factor in how dangerous a hot day is; there's also another measure

Comments are closed.