Social Engineering Attacks How They Work And How To Protect Your

Social Engineering Attacks How They Work And How To Protect Your And this lack of knowledge makes them prime targets for social engineering attacks proactive measures to secure your onboarding process and equipping new employees with the knowledge and tools How Hackers Attack Physical Security Systems, and How Campuses Can Stop Them, campus security, cybersecurity, technology
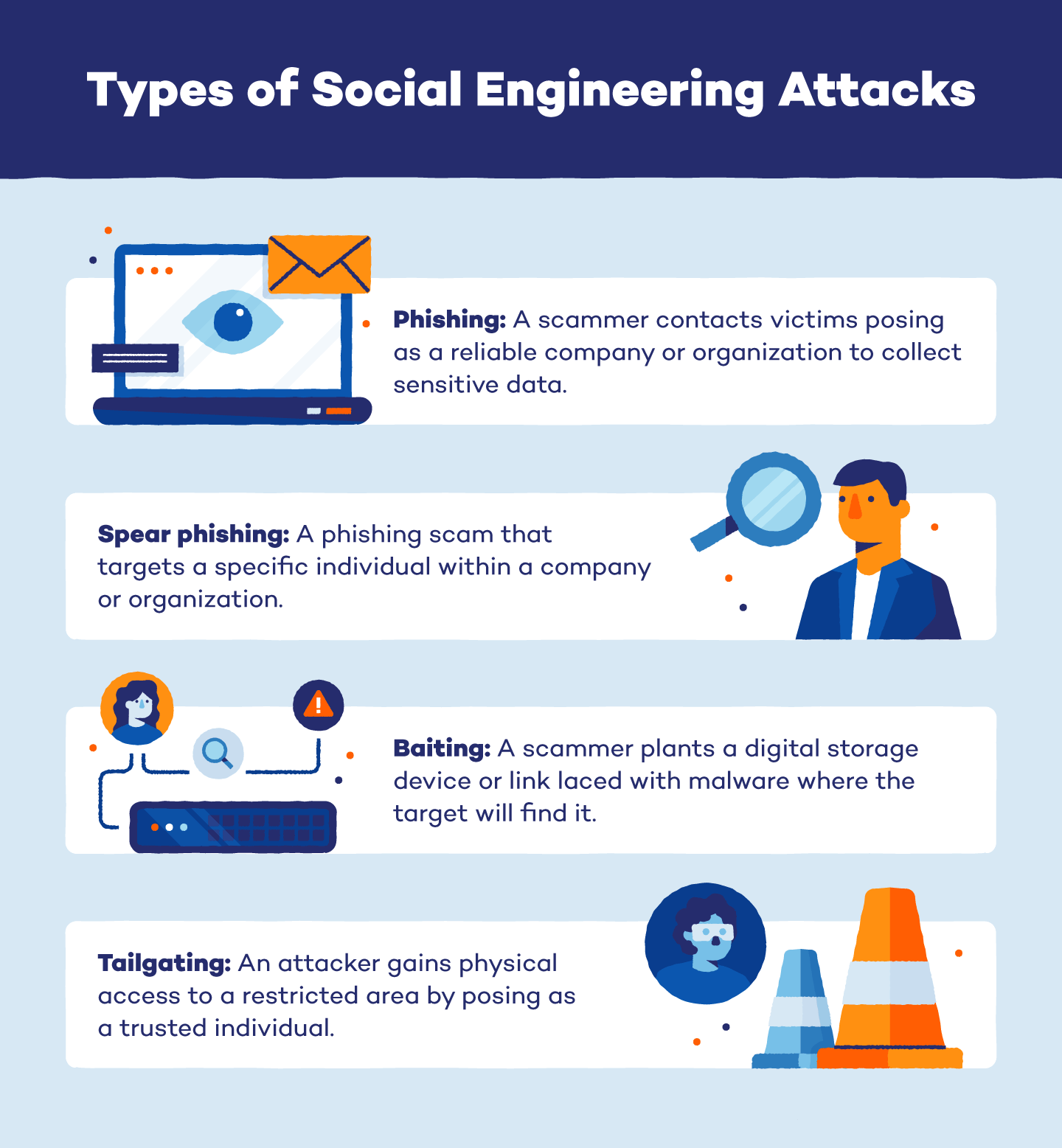
What Is Social Engineering And How Can You Protect Yourself Malware Your online reputation is how people perceive your business based on reviews, social media interactions, and search engine results Learn how to stay safe online with this cyber security awareness guide that takes you through the knowledge and tools you need to navigate CEOs need to rethink trust across the entirety of their organizations of they are to survive the rise of the deepfakes Cybercriminals are increasingly targeting healthcare organizations, but understanding the threats and regulations can help you safeguard sensitive patient data

What Are Social Engineering Attacks And How To Prevent Them Seon CEOs need to rethink trust across the entirety of their organizations of they are to survive the rise of the deepfakes Cybercriminals are increasingly targeting healthcare organizations, but understanding the threats and regulations can help you safeguard sensitive patient data Experts warn of increasing payments due to ransomware Discover the latest insights on this growing cyber threat Business email compromise (BEC) is one of the most damaging and costly cyber attacks against small businesses Stay ahead of cybersecurity threats during election campaigns Discover strategies to protect digital accounts and assets from hackers Technical advances have fundamentally changed the way companies operate and interact with consumers With the proliferation of mobile technology, social media, and the digitization of business
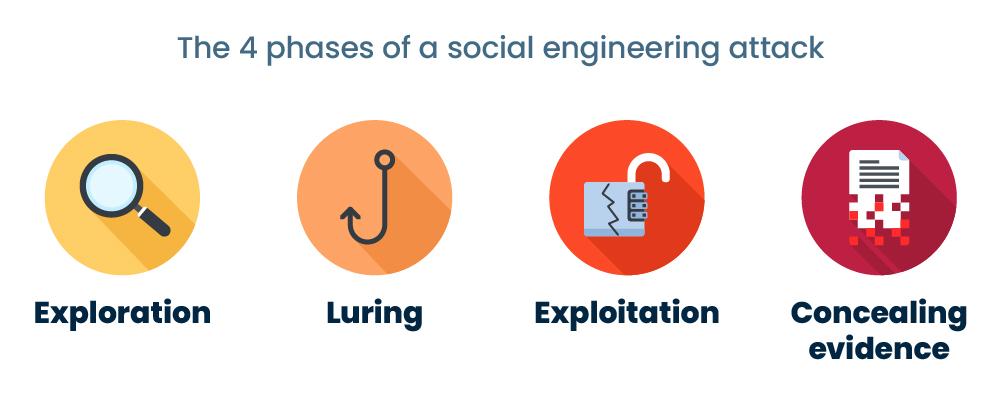
Types Of Social Engineering Attacks And How To Prevent Them With Experts warn of increasing payments due to ransomware Discover the latest insights on this growing cyber threat Business email compromise (BEC) is one of the most damaging and costly cyber attacks against small businesses Stay ahead of cybersecurity threats during election campaigns Discover strategies to protect digital accounts and assets from hackers Technical advances have fundamentally changed the way companies operate and interact with consumers With the proliferation of mobile technology, social media, and the digitization of business But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Given the inadequacy of traditional security measures, financial institutions can no longer rely on isolated defenses like firewalls or antivirus software Instead, a multi-layered security approach
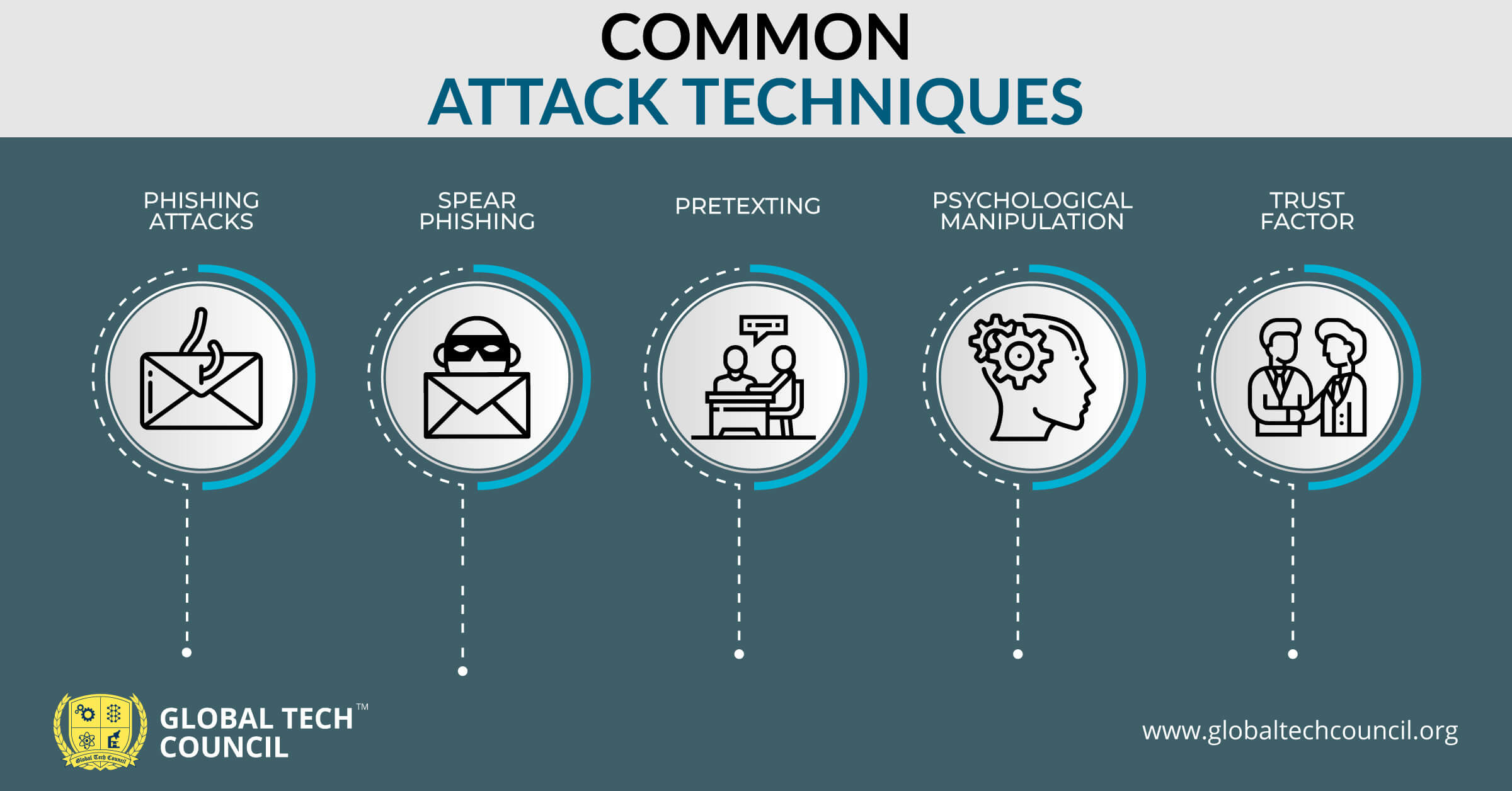
Social Engineering Attacks What They Are And Some Prevention Tips Stay ahead of cybersecurity threats during election campaigns Discover strategies to protect digital accounts and assets from hackers Technical advances have fundamentally changed the way companies operate and interact with consumers With the proliferation of mobile technology, social media, and the digitization of business But God forbid, if it ends up happening to you then how would you know and what would you do? Panic, of course But then? Let us tell you some of the basics of how to know if your phone is hacked and Given the inadequacy of traditional security measures, financial institutions can no longer rely on isolated defenses like firewalls or antivirus software Instead, a multi-layered security approach

Comments are closed.