Some Good Practices To Avoid Social Engineering Attack R Coolgui

Some Good Practices To Avoid Social Engineering Attack Picture based reference guides for anything and everything. if it seems like something someone might print, physically post, and reference then it is a good link for this sub. remember: infographics are learning tools, guides are reference tools. sometimes it's grey. 1. use a robust mfa solution. mfa is a powerful tool in the fight against various types of social engineering threats. it adds extra layers of security to help prevent unauthorized access. mfa requires users to provide two or more verification factors, making it much harder for attackers to gain access.
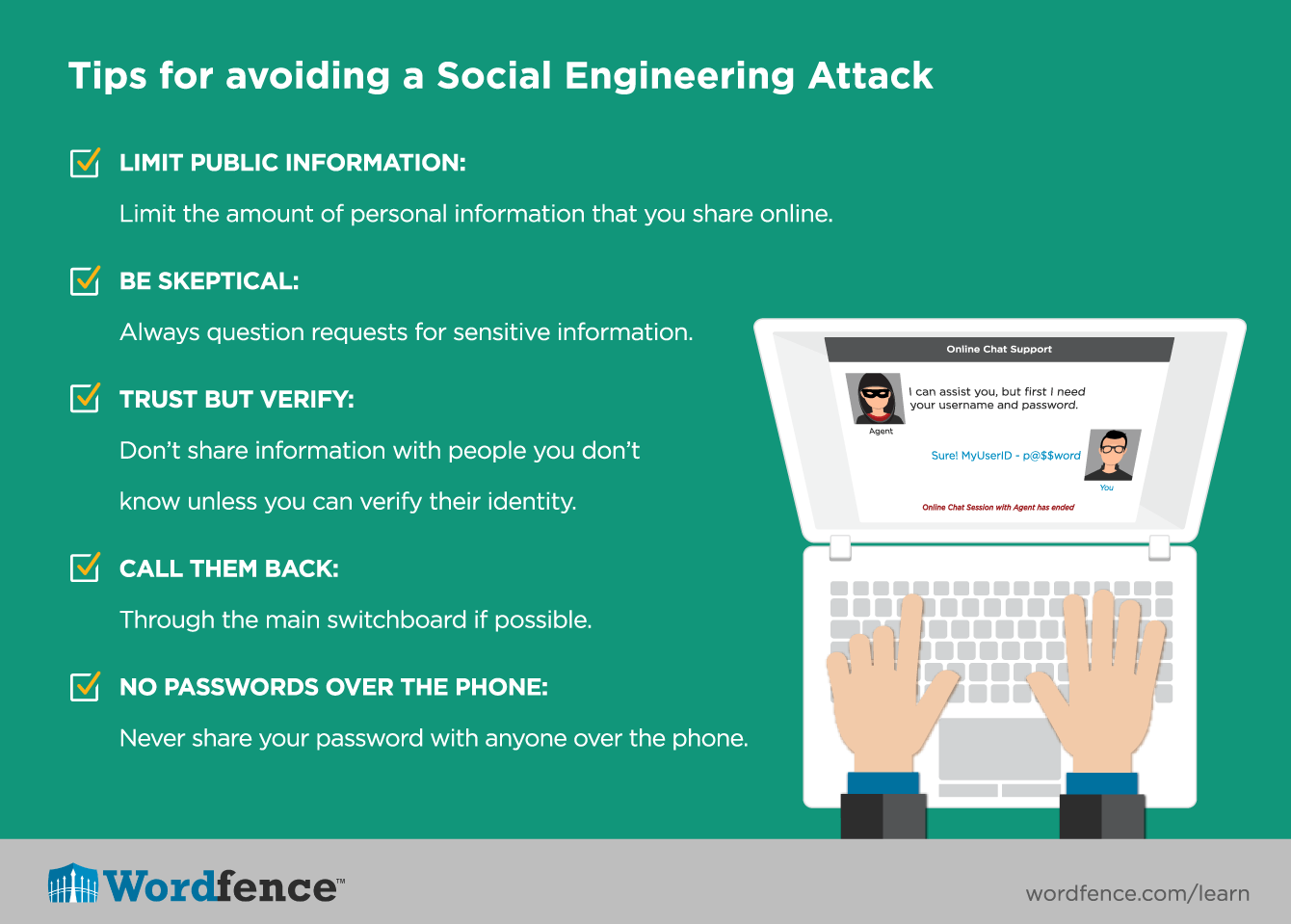
Understanding Social Engineering Techniques Never open strange looking files or attachments. use mfa and vpn services to protect your identity and your communications. 3. put effective technology backstops in place. even organizations with comprehensive policies and procedures and well trained employees have been the victims of social engineering. The threat landscape for social engineering attacks continues to evolve, requiring a proactive and adaptive approach to defense. to stay steps ahead of cybercriminals, businesses and organizations must be vigilant in recognizing and resisting these attacks to mitigate the short term and long term risks they pose. by educating employees and. Social engineering definition. social engineering is an umbrella term that describes a variety of cyberattacks that use psychological tactics to manipulate people into taking a desired action, like giving up confidential information. social engineering attacks work because humans can be compelled to act by powerful motivations, such as money. 4. regularly update and patch systems. keeping your electronic systems up to date will not, in and of itself, prevent social engineering attacks. however, social engineering is often a first volley, followed by measures like ransomware. ensure that your organization’s software is patched and your hardware’s firmware is up to date.

Comments are closed.