Sophos Xg Configuring Site To Site Ipsec Vpn With Failover Group
How To Configure An Ipsec Vpn Failover With Multiple Connections On Network details: fill your local and remote network. step 2: create ipsec connections at bo. go to: system > vpn > ipsec > “add”. connection type: site to site. policy: defaultbranchoffice. action on vpn restart: initiate. authentication type: any (preshared key is my option) endpoints details: you need add an endpoint. Working remotely continues to be a key option for today's workforce, but how do you ensure your secure vpn connections are reliable?in this tutorial video, f.
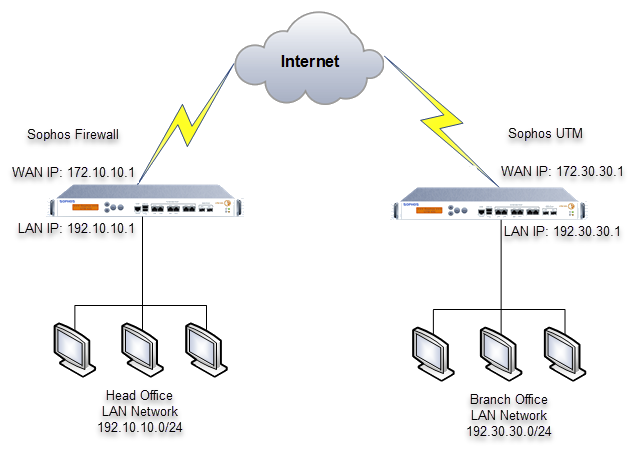
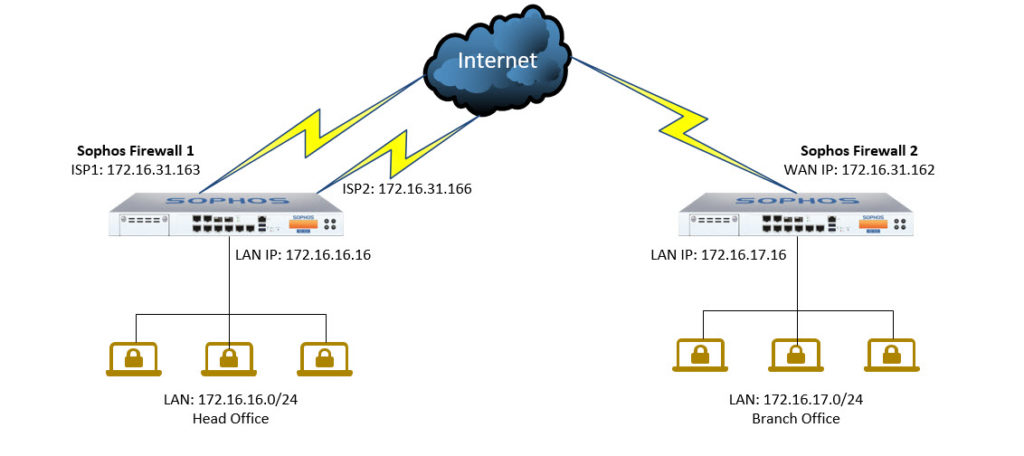
Sophos Firewall Configure A Site To Site Ipsec Vpn Connection Between Got a quick question for the experts out there. i'm trying to set up an ipsec vpn failover group between two xgs firewalls, hq and branch, each with two wan connections. i created 4 tunnels (two for each wan connection) and added them to a failover group on both firewalls. however, when the groups on both firewalls are enabled, they can't. This article focuses on the best practices to plan and configure a site to site policy based ipsec vpn. it can be applied in general and is not limited to the sophos firewall. configure the vpn connection 1. configure only one vpn gateway as initiator. it is recommended to configure one vpn gateway as a vpn initiator and the other as a vpn. To verify this, we can check the status of the tunnel in the ipsec overview section by going to configure>site to site vpn>ipsec tab. hq. separate site location. xfrm interface mapping recommendation. xfrm interfaces are like a long cable between two appliances, and both ends of the tunnel require an ip address. Sophos xg series: ho: 1 wan link bo: 2 wan links i created 2 vpn tunnels from bo to hothanks for watching!.

Tutorial Sophos Xg Firewall Konfigurasi Failover Ipsec Vpn Site To verify this, we can check the status of the tunnel in the ipsec overview section by going to configure>site to site vpn>ipsec tab. hq. separate site location. xfrm interface mapping recommendation. xfrm interfaces are like a long cable between two appliances, and both ends of the tunnel require an ip address. Sophos xg series: ho: 1 wan link bo: 2 wan links i created 2 vpn tunnels from bo to hothanks for watching!. This week we demonstrate how to set up an ipsec vpn failover group on your sophos xg firewall running sfos 17.5. this means greater availability and redundan. Go to vpn > ipsec connections. scroll to failover group and click add. enter a name. select at least two connections. if the primary connection fails, the next active connection in the group automatically takes over. note. the ip address of the remote id must be the same for all connections in the group. select mail notification to receive.

Comments are closed.