Targeted Zero Trust New Dod Strategy Will Outline 90 Capabilities
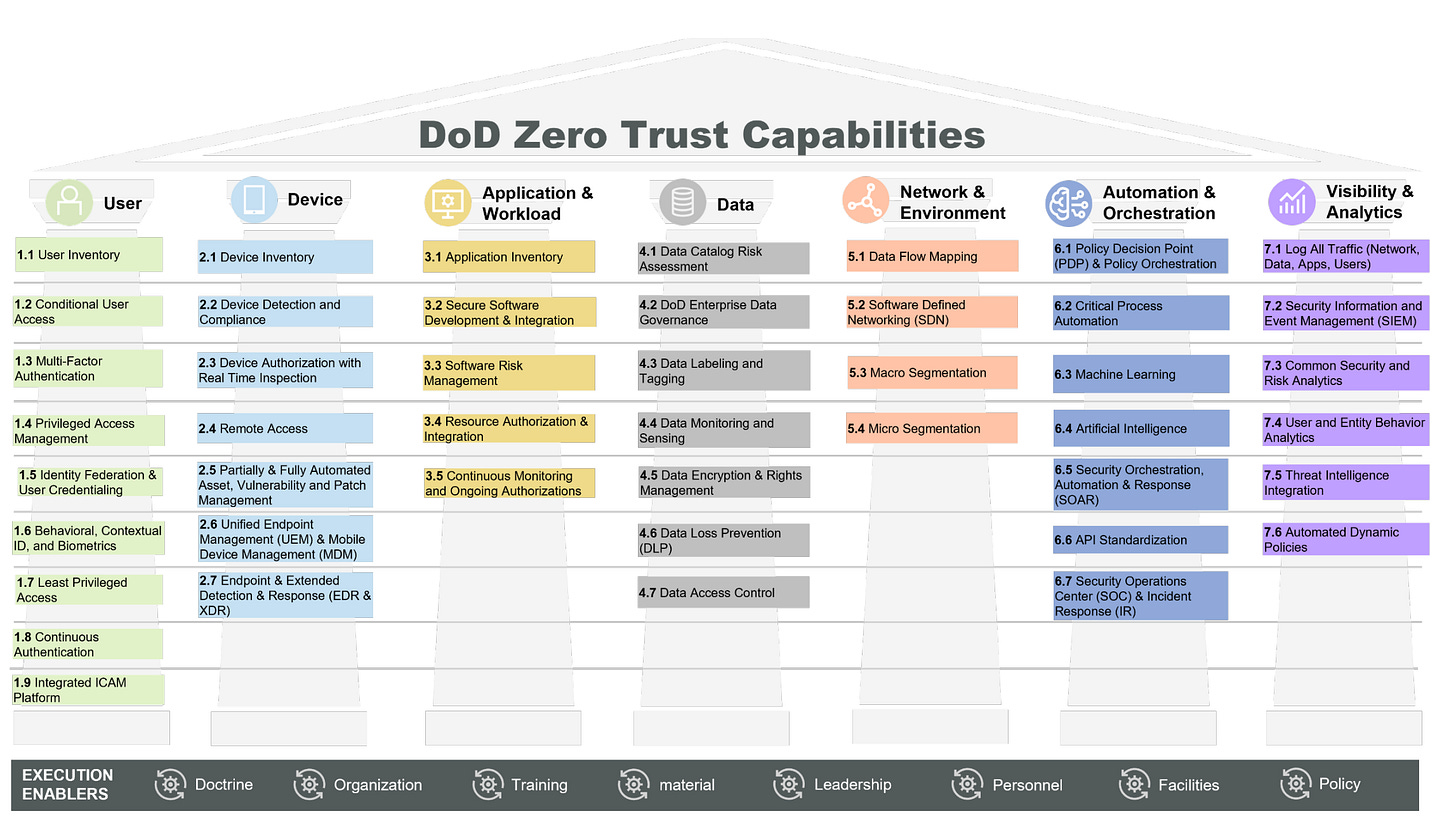
A Look At The Dod S Zero Trust Strategy By Chris Hughes The strategy outlines 90 capabilities that will get the pentagon after what it's calling targeted zero trust and an additional 62 capabilities for a more "advanced" zero trust, david mckeown, dod. Zt ca abilities in bold font and dis la ed on the zt target line contain activities s anning both target and advanced zt as of 2 22. once capabilities are broken out into activities, zt target level and advanced zt provide a much more definitive path to execution. coa 1 (dod baseline) achieves target.
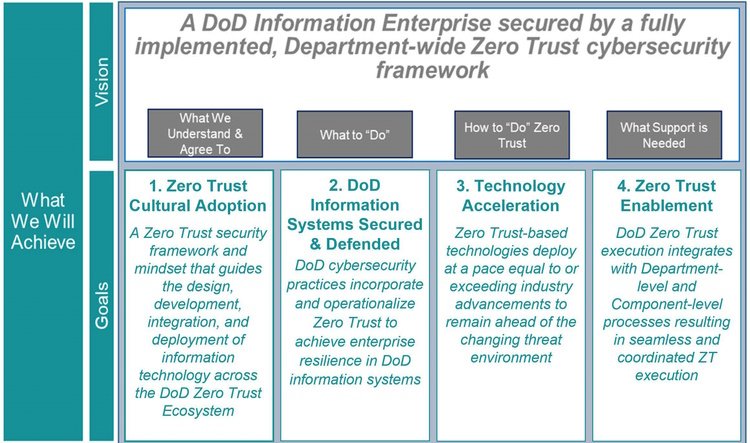
Exploring The New Department Of Defense Dod Zero Trust Strategy Zscale It also includes three methods to bring to bear the pentagon’s targeted zero trust goal, including “uplifting the current environment of each military service and agency to meet the 90 capabilities and achieve the highest level of zero trust.” dod prepares to implement new zero trust strategy, data challenge expected on day one of the. The strategy envisions a dod information enterprise secured by a fully implemented, department wide zero trust cybersecurity framework that will reduce the attack surface, enable risk management. The dod released its formal zero trust strategy in october 2022. 1 the strategy is a security framework and mindset that set a path for achieving zero trust. the strategy outlines strategic goals for adopting culture, defending dod information systems, accelerating technology implementation, and enabling zero trust. This strategy lays out the department's vision for zero trust and sets a path to achieve it. it includes the strategic assumptions and principles that will inform and guide the adoption of zt and the strategic goals and objectives. the four strategic goals outlined in this strategy are: 1.

A Peek Into The Newly Released Dod Zero Trust Strategy Part 1 Of 2 The dod released its formal zero trust strategy in october 2022. 1 the strategy is a security framework and mindset that set a path for achieving zero trust. the strategy outlines strategic goals for adopting culture, defending dod information systems, accelerating technology implementation, and enabling zero trust. This strategy lays out the department's vision for zero trust and sets a path to achieve it. it includes the strategic assumptions and principles that will inform and guide the adoption of zt and the strategic goals and objectives. the four strategic goals outlined in this strategy are: 1. Along with the 91 activities that are needed to reach target zero trust, advanced levels will require an additional 61 activities, according to the dod’s strategy. “this is not a one and done. we’ve got the target level zero trust and then the broader implementation of zero trust five years later,” sherman said. 1 user. capability description. dod organizations and overall enterprise employ enterprise level identity management and public key infrastructure (pki) systems to track user, administrator and npe identities across the network and ensure access is limited to only those who have the need and the right to know.

ташюааtargetedтащ Zero Trust New Dod Strategy Will Outline 90 Capabilitiesюаб Along with the 91 activities that are needed to reach target zero trust, advanced levels will require an additional 61 activities, according to the dod’s strategy. “this is not a one and done. we’ve got the target level zero trust and then the broader implementation of zero trust five years later,” sherman said. 1 user. capability description. dod organizations and overall enterprise employ enterprise level identity management and public key infrastructure (pki) systems to track user, administrator and npe identities across the network and ensure access is limited to only those who have the need and the right to know.

Dod Zero Trust Strategy Industrial Cyber

Comments are closed.