Tenable Nessus Byol Scanner Aws Integration Guide
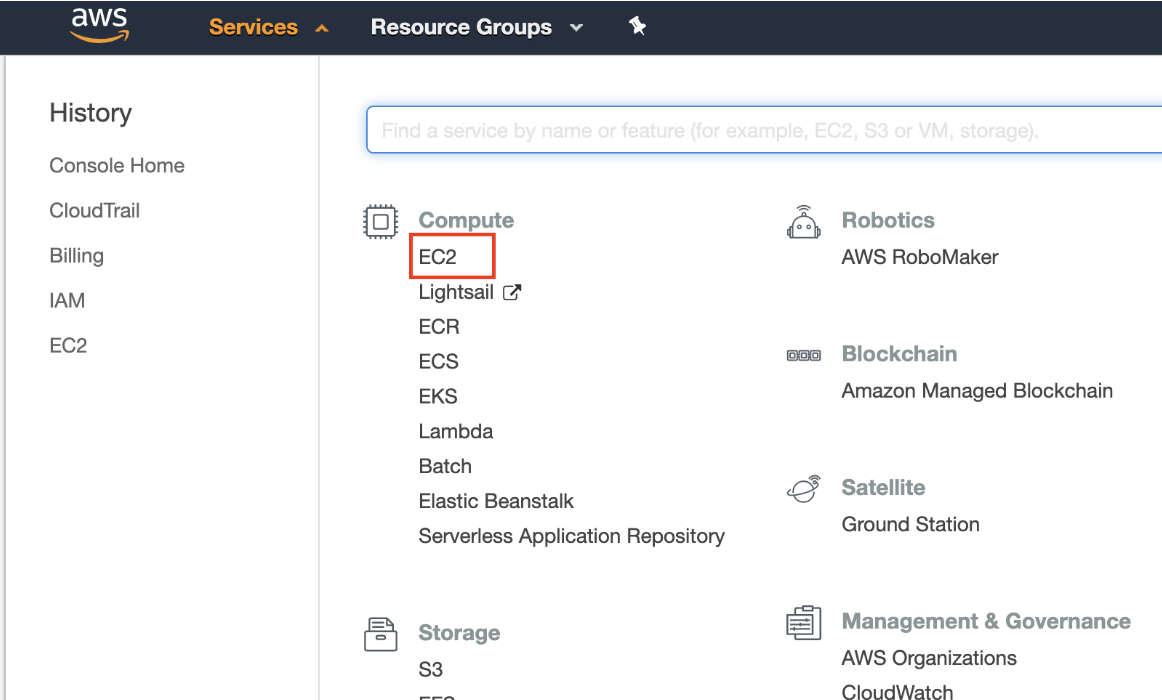
Tenable Nessus Byol Scanner Aws Integration Guide In the left panel, click aws marketplace. in the search box, type nessus. on your keyboard, press enter. in the nessus (byol) section, click select. the nessus (byol) review window appears. review the pricing details and instance type details. click continue. the step 2: choose an instance type page appears. click next: configure instance details. To activate the tenable nessus byol scanner (tenable nessus expert or tenable nessus professional): navigate to the tenable nessus user interface on port 8834, for example, <nessusbyol ip>:8834, where <byolpublicip> is the ip address of your tenable nessus expert or tenable nessus professional instance. the.
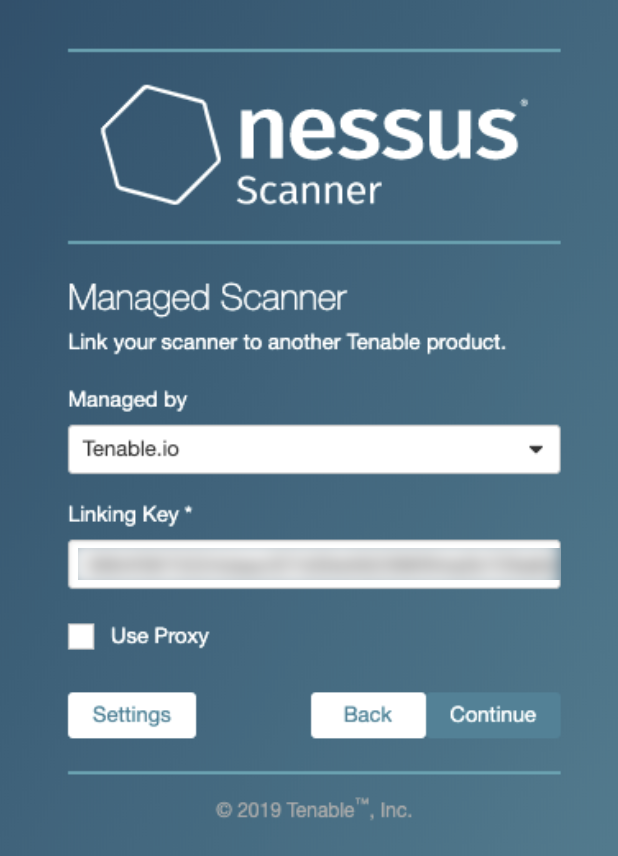
Activate Tenable Nessus Byol Scanner Linked To Tenable Vulnerability Integration configuration. to configure aws for tenable vulnerability management, see the following integration configuration topics: tenable nessus byol scanner. activate the nessus byol scanner. activate tenable nessus byol scanner via the command line; obtain tenable vulnerability management linking key. For more information, see the nessus user guide. to confirm the nessus byol scanner in tenable vulnerability management: log in to tenable vulnerability management. in the top menu bar, click scans. the my scans page appears. in the left hand menu, click scanners. the scanners page appears. confirm the byol scanner appears in the linked. To activate the tenable nessus professional byol scanner via the command line: adjust the permissions for your downloaded ssh key using the following command: chmod 400 mynessuskey.pem. ssh into the nessus byol scanner using the following command: ssh i mynessuskey.pem ec2 user@<byolpublicip>. where <byolpublicip> is the ip address of your. When you link the scanner to tenable vulnerability management using the command line, as described in the link to tenable vulnerability management topic in the tenable nessus user guide, use the optional aws scanner flag. for example: > nessuscli managed link key=<linking key> cloud. the scanner must already be running on an aws instance.

Activate Tenable Nessus Byol Scanner Linked To Tenable Vulnerability To activate the tenable nessus professional byol scanner via the command line: adjust the permissions for your downloaded ssh key using the following command: chmod 400 mynessuskey.pem. ssh into the nessus byol scanner using the following command: ssh i mynessuskey.pem ec2 user@<byolpublicip>. where <byolpublicip> is the ip address of your. When you link the scanner to tenable vulnerability management using the command line, as described in the link to tenable vulnerability management topic in the tenable nessus user guide, use the optional aws scanner flag. for example: > nessuscli managed link key=<linking key> cloud. the scanner must already be running on an aws instance. Ssh into the nessus byol scanner using the following command: ssh i mynessuskey.pem ec2 user@<byolpublicip> where <byolpublicip> is the ip address of your tenable nessus byol instance. elevate privileges using the following command: sudo su. update the ami using the following command: yum update y. Anyone successfully deploy the tenable preauthorized or byol scanner to aws using the standard aws automation tools such as aws cli[1] tool or using a cloudformation[2] template? if so, did you document the procedure and are you able to share it somewhere like github? it will help many others save time in deployment.

Comments are closed.