Tips For Avoiding Data Breach In Your Business
Preventing Data Breaches Best Practices Tupa Privileged access management tools can help facilitate and enforce these policies. it's not difficult to convince business leaders that a data breach can cause tremendous pain. 3. patch infrastructure. the patching of networks and systems should be a top priority for any it security team. 1. restrict access. each person who has access or potential access to data is another vulnerability. if there are 1,000 people logging into a system that has personal information, there are 1,000.
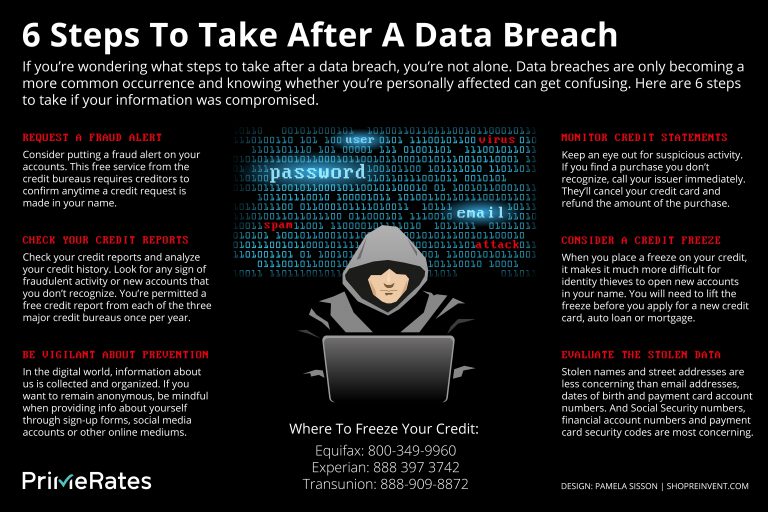
Infographic What To Do After A Data Breach Primerates A simple yet effective data breach prevention strategy involves adding resistance to the cyberattack pathway to make it increasingly difficult for hackers to progress toward their data theft objective. this strategy can be broken down into two stages. stage 1 preventing network compromise. stage 2 preventing access to sensitive data. 2. outline clear and concise data security policies. data security policies specify the administration, handling, and usage of data within an organization to safeguard information and prevent data breaches. they help employees understand their level of access to and responsibility for business data. A containment strategy: steps like unplugging impacted systems from the network or shutting down vulnerable servers should be included to limit the breach and prevent future harm. a recovery strategy: steps to recover from the data breach should be included in the strategy, such as recovering data from backups and adopting new security measures. 1. bring in a cybersecurity specialist. educate your firm on past data breaches by bringing in a cybersecurity specialist to speak about best practices and how to keep security top of mind. the.

A юааbusinessюаб Ownerтащs Guide To юааavoidingюаб юааdataюаб юааbreachюаб The юааbusinessюаб Econom A containment strategy: steps like unplugging impacted systems from the network or shutting down vulnerable servers should be included to limit the breach and prevent future harm. a recovery strategy: steps to recover from the data breach should be included in the strategy, such as recovering data from backups and adopting new security measures. 1. bring in a cybersecurity specialist. educate your firm on past data breaches by bringing in a cybersecurity specialist to speak about best practices and how to keep security top of mind. the. In a hyper connected business world, organizational leaders understand that data breaches are a fact of life. however, these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively. 1. identity sensitive data collected, stored, transmitted, or processes. before you can prevent a data breach. Below is a round up of the most notable data breach prevention best practices: 1. have a tried and tested incident response plan (irp) in place. an incident response plan that has been tested, retested and perfected, will really help you reduce the time it takes to detect and respond to a data breach. it can help reduce the potential costs of a.

Tips For Avoiding Data Breach In Your Business In a hyper connected business world, organizational leaders understand that data breaches are a fact of life. however, these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively. 1. identity sensitive data collected, stored, transmitted, or processes. before you can prevent a data breach. Below is a round up of the most notable data breach prevention best practices: 1. have a tried and tested incident response plan (irp) in place. an incident response plan that has been tested, retested and perfected, will really help you reduce the time it takes to detect and respond to a data breach. it can help reduce the potential costs of a.

Comments are closed.