Types Of Social Engineering Attacks

6 Types Of Social Engineering Attack Powerpoint Presentation Images Learn how cybercriminals manipulate human behavior to steal sensitive data, credentials, access devices and more. discover the common tactics, examples and prevention tips for phishing, whaling, baiting, diversion theft and other social engineering attacks. Learn how hackers use phishing, imposter frauds, and other scams to manipulate you into giving them what they want. find out the 12 most common types of social engineering attacks and how to protect yourself from them.

What Are Social Engineering Attacks Learn how phishing, clone phishing, pretexting, baiting, and other social engineering techniques work and how to prevent them. see real life examples of successful and failed attacks and best practices for organizations. Learn how social engineers use manipulative tactics to trick victims into disclosing private information or performing desired actions. find out the six types of social engineering attacks, such as phishing, vishing, pretexting, baiting, tailgating, and quid pro quo. Learn what social engineering is and how it exploits human psychology to gain access to buildings, systems, or data. see examples of common social engineering attacks, such as phishing, impersonation, and authority abuse. Learn how social engineers manipulate trust and human behavior to carry out security breaches. find out the stages, motivations and examples of social engineering attacks and how to protect yourself and your organization.

Watch Out 8 Types Of Social Engineering Attacks And How To Avoid Them Learn what social engineering is and how it exploits human psychology to gain access to buildings, systems, or data. see examples of common social engineering attacks, such as phishing, impersonation, and authority abuse. Learn how social engineers manipulate trust and human behavior to carry out security breaches. find out the stages, motivations and examples of social engineering attacks and how to protect yourself and your organization. While the term social engineering covers any type of psychological trickery designed to elicit money or personal data, attacks tend to fall into one of several patterns. the most common types of. Learn what social engineering is, how it works, and what types of attacks use it. see examples of phishing, baiting, pretexting, and more, and how to protect yourself and your organization.
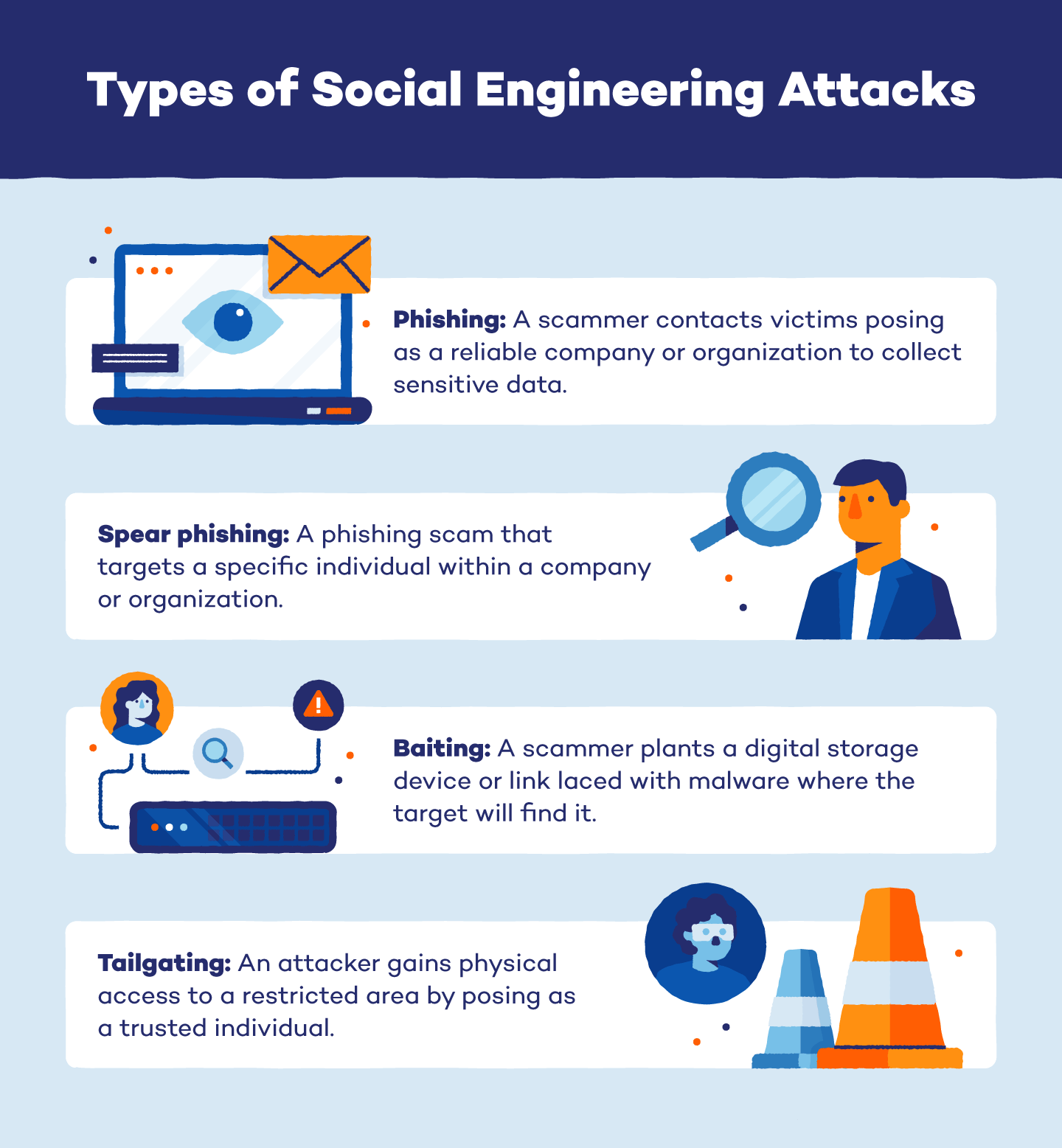
What Is Social Engineering And How Can You Protect Yourself Malware While the term social engineering covers any type of psychological trickery designed to elicit money or personal data, attacks tend to fall into one of several patterns. the most common types of. Learn what social engineering is, how it works, and what types of attacks use it. see examples of phishing, baiting, pretexting, and more, and how to protect yourself and your organization.
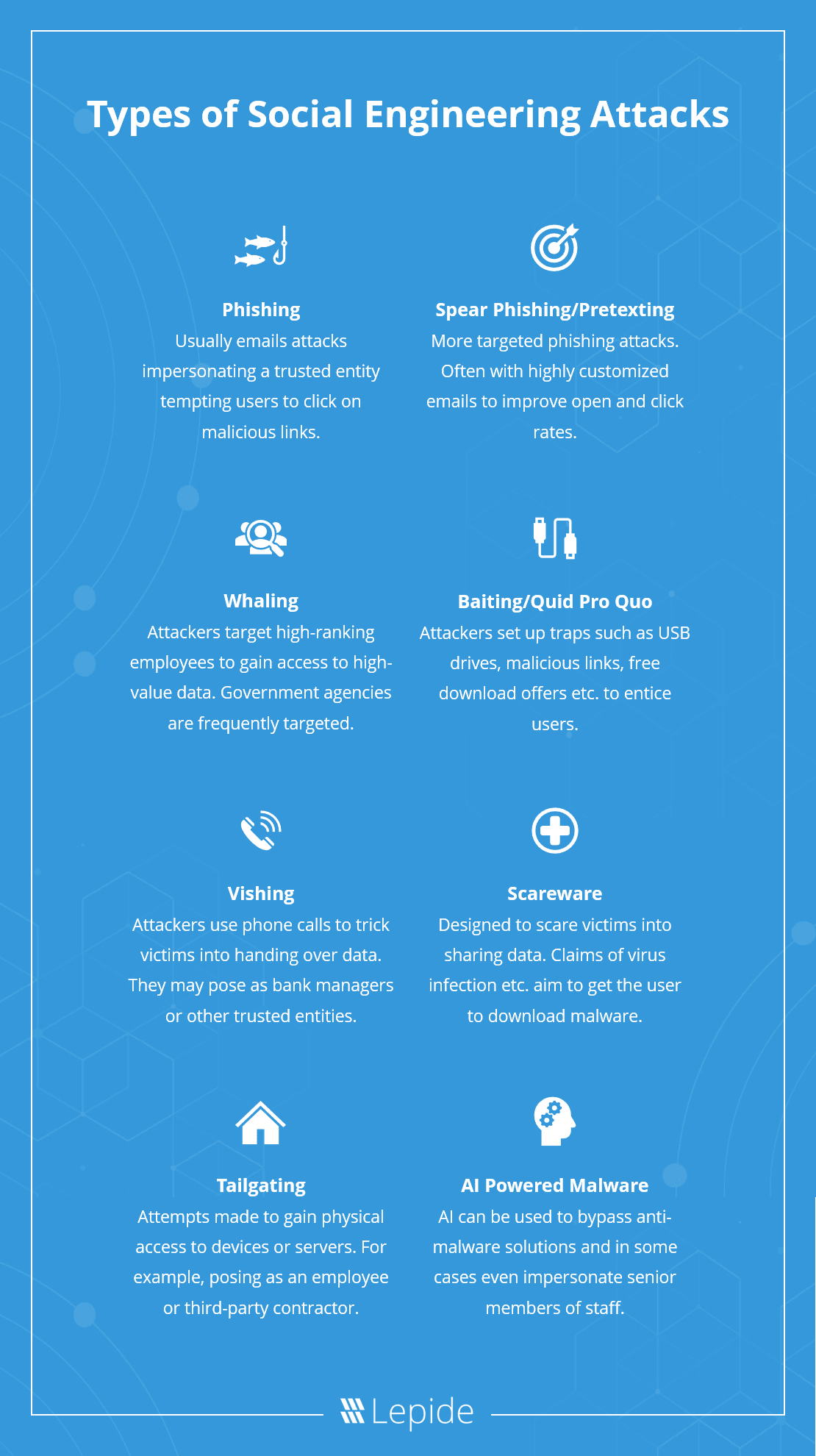
The Complete Guide To Social Engineering Attacks

Comments are closed.