What Is Digital Security Assessing Your Risks With The Threat Model
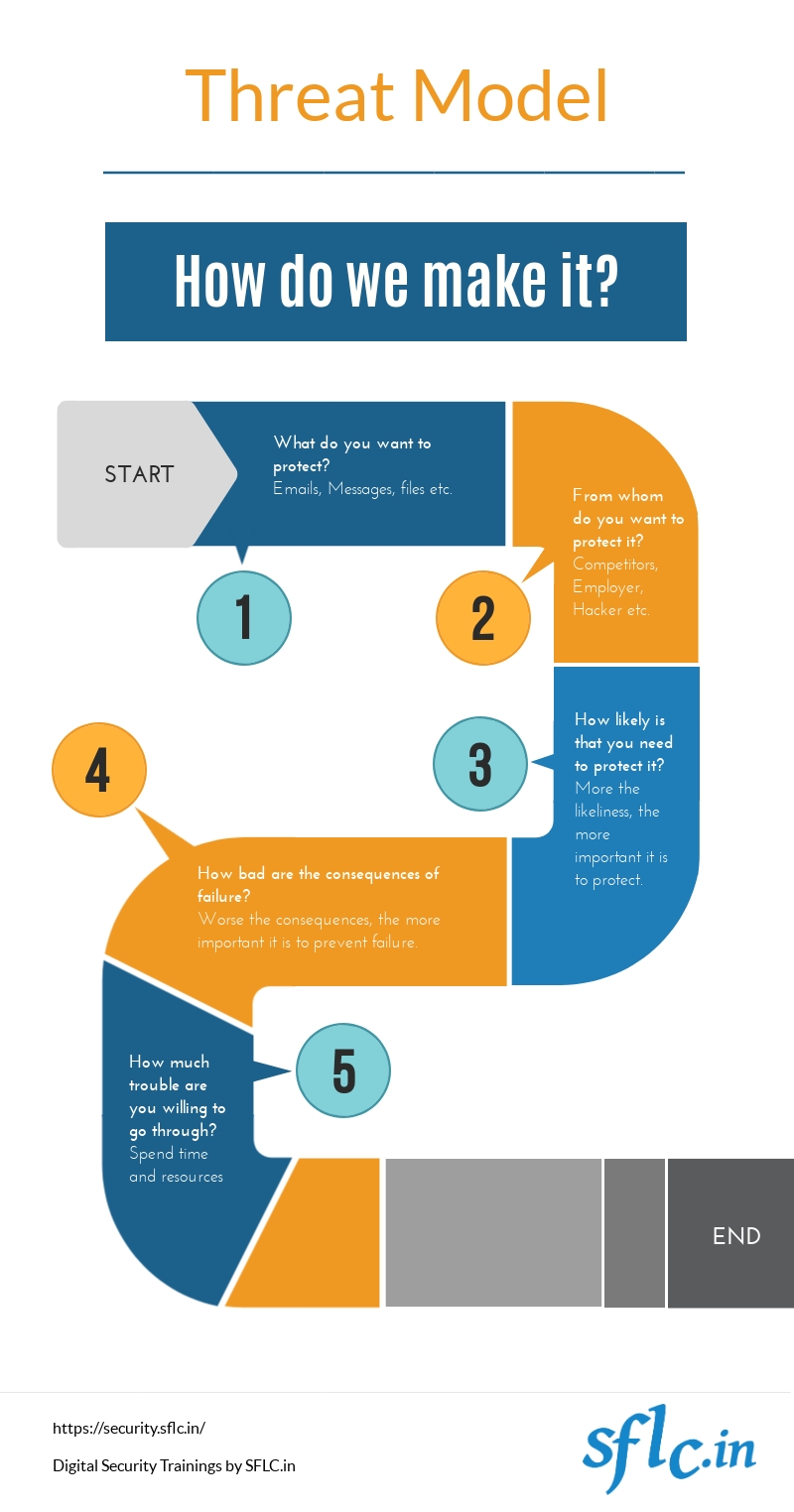
What Is Digital Security Assessing Your Risks With The Threat Model Pasta threat modeling pasta, which stands for process for attack simulation and threat analysis, is a seven step process focused on aligning technical security requirements with business. Threat modeling evaluates threats and risks to information systems, identifies the likelihood that each threat will succeed and assesses the organization’s ability to respond to each identified threat. 1. identifying security requirements and vulnerabilities. the threat modeling process requires identifying security requirements and security.

What Is Digital Risk Management A Definition By Upguard Threat modeling is the process of identifying and sharing information about cybersecurity threats that can affect a given network or system. modeling security threats helps it teams understand their nature and potential impact on the organization. it also facilitates the analysis of threats to determine their risks to the organization’s apps. Threat modeling is the process of using hypothetical scenarios, system diagrams, and testing to help secure systems and data. by identifying vulnerabilities, helping with risk assessment, and suggesting corrective action, threat modeling helps improve cybersecurity and trust in key business systems. threat trends report. Firstly, many developers lack sufficient knowledge and experience in the field of security, which hinders their ability to effectively use methodologies and frameworks, identify, and model threats. without proper training and understanding of basic security principles, developers may overlook potential threats or incorrectly assess their risks. The visual, agile, and simple threat (vast) model is a security method that assumes the attacker has an unlimited number of ways to attack. it was developed by bruce schneier, a well known american cryptographer. the vast model allows security teams to assess risk from two different perspectives architectural and operational.

What Is Cyber Threat Modeling Importance Of Threat Modeling Ec Council Firstly, many developers lack sufficient knowledge and experience in the field of security, which hinders their ability to effectively use methodologies and frameworks, identify, and model threats. without proper training and understanding of basic security principles, developers may overlook potential threats or incorrectly assess their risks. The visual, agile, and simple threat (vast) model is a security method that assumes the attacker has an unlimited number of ways to attack. it was developed by bruce schneier, a well known american cryptographer. the vast model allows security teams to assess risk from two different perspectives architectural and operational. Threat modeling involves decomposing the system and identifying key risk related components including assets, threat agents, attack vectors, and security controls. threat modeling is not a method for code reviewing or penetration testing but, since it outputs risks, it can help drive a range of risk based activities. An advanced data driven strategy of your threat assessment can include risk modeling, where an ai model can learn how your systems behave in response to cybersecurity threats. this can be a crucial part of your threat assessment projects where you can identify, predict and test known and known security risks and vulnerabilities.
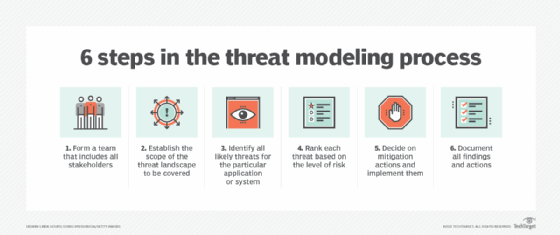
What Is Threat Modeling Threat modeling involves decomposing the system and identifying key risk related components including assets, threat agents, attack vectors, and security controls. threat modeling is not a method for code reviewing or penetration testing but, since it outputs risks, it can help drive a range of risk based activities. An advanced data driven strategy of your threat assessment can include risk modeling, where an ai model can learn how your systems behave in response to cybersecurity threats. this can be a crucial part of your threat assessment projects where you can identify, predict and test known and known security risks and vulnerabilities.

Security Modeling And Threat Modeling Resources Cybersecurity Memo

Comments are closed.