What Is Pretexting Attack Types Examples Imperva 47 Off

What Is Pretexting Attack Types Examples Imperva 47 Off Pretexting definition. pretexting is a certain type of social engineering technique that manipulates victims into divulging information. a pretext is a made up scenario developed by threat actors for the purpose of stealing a victim’s personal data. during pretexting attacks, threat actors typically ask victims for certain information. Here are a few types of pretexting attacks you should be aware of: piggybacking: piggybacking occurs when an authorized person allows a threat actor to use their credentials, often by assisting them in gaining physical access to a restricted area based on a believable pretext. business email compromise: business email compromise (bec) is.
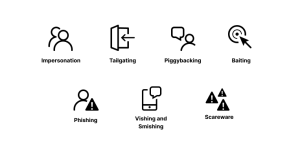
Types Of Pretexting Attacks Pretexting definition. pretexting is a form of social engineering tactic used by attackers to gain access to information, systems, or services by creating deceptive scenarios that increase the success rate of a future social engineering attack. social engineering refers to when a hacker impersonates someone the victim knows or trusts—such as. Pretexting is form of social engineering in which an attacker tries to convince a victim to give up valuable information or access to a service or system. the distinguishing feature of this kind. Pretexting is a form of social engineering attack in which a scammer creates a plausible scenario to bait victims into divulging sensitive information, making fraudulent payments, granting access to an account, and so on. closely related to various types of phishing, pretexting scams are characterized by detailed situations (pretexts) and often. Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages.

Comments are closed.