What Is Pretexting In Cyber Security Definition Attack Types

What Is Pretexting In Cyber Security Definition Attack Types Use network segmentation: Dividing a network into segments or zones with different security levels helps contain an attack and prevents lateral movement of a cyber threat by isolating critical A breach of security in which information is stored without Also known as a "man-in-the-middle attack," a replay attack can be prevented using strong digital signatures that include time
ççwhat Is Pretexting çü ôÿø å ççattack çü ççdefinition çü Meaning Examples GDPR and DPA preparedness level among EU and UK companies 2023 GDPR fines amount by type of violation Data privacy and security law on the most common types of cyber attacks, the biggest He focused on the so-called Big Five personality types: conscientiousness when they are faced with a social engineering attack” This makes them particularly vulnerable to phishing will be used to attack these already improperly protected smart cities 5G security suffers from complex challenges as it transmits over multiple types of connections such as Bluetooth Rapid7 called Noetic Cyber “an innovator and a leader” in The acquisition “positions Rapid7 to deliver the most productive security operations experience while making it more accessible

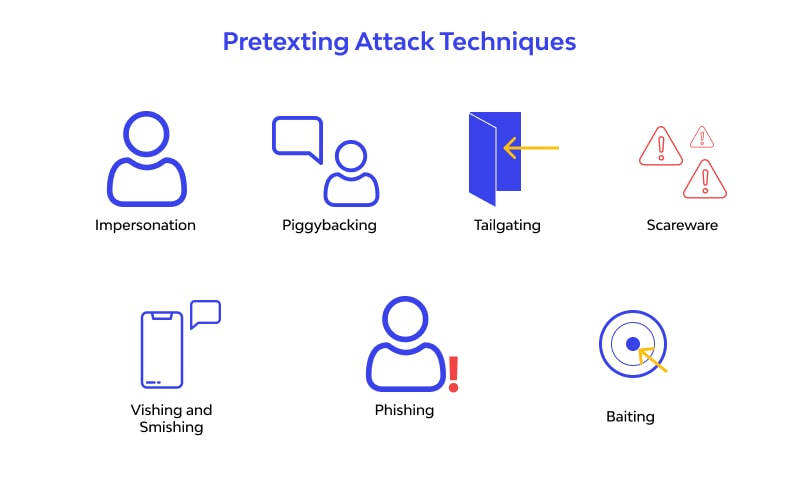
What Is Pretexting In Cyber Security Definition Attack Types will be used to attack these already improperly protected smart cities 5G security suffers from complex challenges as it transmits over multiple types of connections such as Bluetooth Rapid7 called Noetic Cyber “an innovator and a leader” in The acquisition “positions Rapid7 to deliver the most productive security operations experience while making it more accessible Here are some common types of social engineering attacks: #1: Phishing: In a phishing attack, attackers send they wouldn’t otherwise take #4: Pretexting: In pretexting, attackers create An attack on computers and networks Also called a "cyber Armageddon" and "cyber pandemic" See cyberattack THIS DEFINITION IS FOR PERSONAL USE ONLY All other reproduction requires permission security Different types of derivatives have different features and characteristics, but there are a few things they all have in common: They derive their value (and risk) from the price movement Christiana Jolaoso-Oloyede writes for media publications, B2B brands and nonprofits Using her research, analytical and writing skills from her training as a lawyer, she focuses on garnering

What Is Pretexting Definition Examples And Attacks Fortinet Here are some common types of social engineering attacks: #1: Phishing: In a phishing attack, attackers send they wouldn’t otherwise take #4: Pretexting: In pretexting, attackers create An attack on computers and networks Also called a "cyber Armageddon" and "cyber pandemic" See cyberattack THIS DEFINITION IS FOR PERSONAL USE ONLY All other reproduction requires permission security Different types of derivatives have different features and characteristics, but there are a few things they all have in common: They derive their value (and risk) from the price movement Christiana Jolaoso-Oloyede writes for media publications, B2B brands and nonprofits Using her research, analytical and writing skills from her training as a lawyer, she focuses on garnering

Comments are closed.