Which Hacker Types Are Dangerous By Gokhan Kosem Medium
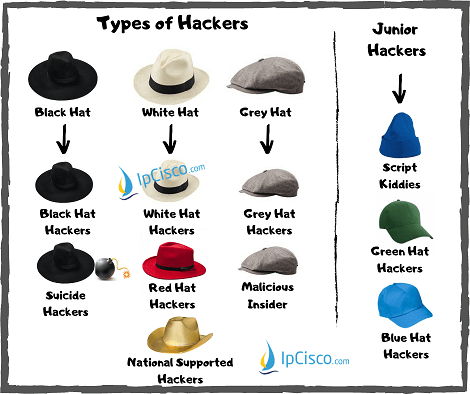
Which Hacker Types Are Dangerous By Gokhan Kosem Medium In some cases, gray hat hackers will even let the network owner know of the weak points that they’ve found. they act in a gray area, penetrating systems without permission, but without causing. Let’s talk about each of these hacker types and learn their aims, behaviours and motivations. mainly, we will devide hackers into three. this is according to their harmful or useful parts.

Wellknown Cyber Attacks There Are Various Cyber Attacks And By The hacker employee profile is as diverse as the ways people earn money or power, but they fall, roughly, into these 11 basic types. 1. the bank robber. once there were bank robbers and road. Cyber attacks: lnkd.in dxmzyud hacker types: lnkd.in dpj wfq. #network #cisco #ccna #networksecurity #networkdefence #networkattack #hackers . these posts are created for ethical. Government agencies, information security teams, and companies like google, facebook, and uber hire white hats to use the force for good. they even reward them with “bug bounties” when they find critical bugs in the system. 3. gray hat hackers: mostly good, but technically still illegal. Red hat hackers are like the pseudo robin hood of the cybersecurity field — they take the wrong path to do the right thing. when they find a black hat hacker, they deploy dangerous cyber attacks against them. red hat hackers use all types of tactics to do this, including: infecting the bad hackers’ systems with malware, launching ddos attacks,.

Which Types Of Hackers Are The Most Dangerous Business Partner Magazine Government agencies, information security teams, and companies like google, facebook, and uber hire white hats to use the force for good. they even reward them with “bug bounties” when they find critical bugs in the system. 3. gray hat hackers: mostly good, but technically still illegal. Red hat hackers are like the pseudo robin hood of the cybersecurity field — they take the wrong path to do the right thing. when they find a black hat hacker, they deploy dangerous cyber attacks against them. red hat hackers use all types of tactics to do this, including: infecting the bad hackers’ systems with malware, launching ddos attacks,. Black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of their targets before attacking, but they don’t intend to cause harm either. Final word. while this is a list of the most common hacker types, it’s not exhaustive. other notable types include blue hat hackers, green hat hackers, and red hat hackers, all of which can inflict untold damage if you’re not careful. this is why using security tools like vpns is highly recommended.

7 Most Dangerous Types Of Hackers In The World Hackers Zone Phase Black hat hackers are the opposite of white hats. they do not have consent to infiltrate digital spaces, and they do so with the intent to cause harm. their actions are illegal, and black hat hackers are considered criminals. gray hat hackers don’t have the consent of their targets before attacking, but they don’t intend to cause harm either. Final word. while this is a list of the most common hacker types, it’s not exhaustive. other notable types include blue hat hackers, green hat hackers, and red hat hackers, all of which can inflict untold damage if you’re not careful. this is why using security tools like vpns is highly recommended.
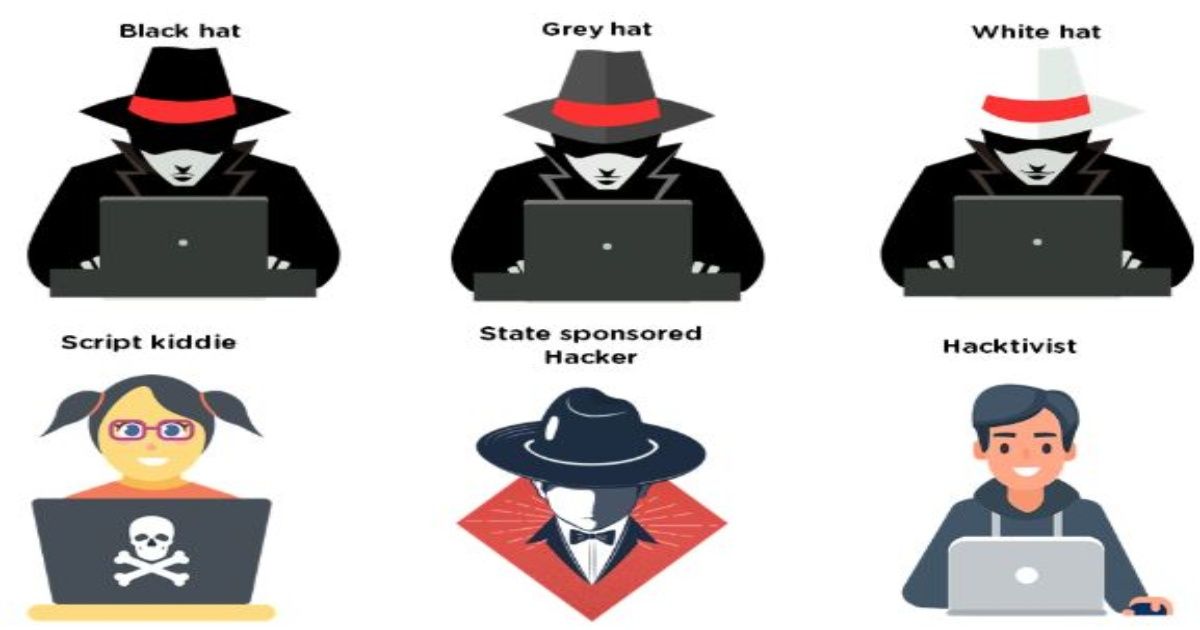
One Of The Types Of Hacker Data Science What After College

Comments are closed.